Cloud Risk Posture
Identify Security, Risk, Compliance, and Productivity gaps in your remote work strategy.
Surface enterprise-wide endpoint vulnerability and risk data in less than a minute.
Understand where a breach is likely to occur, the probability it will occur, and how severe it will be. Using telemetry and data streams from a number of sources and sensors - the modern CISO can now view risk maps by region, group, organization, or other logical or observed definition.
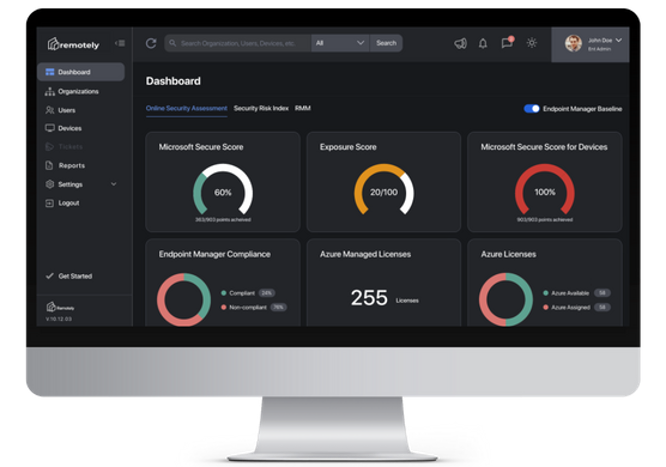
Your Microsoft Secure Score is an aspirational value of your User, Data, Device, and Identity Risk provided by Microsoft, in analysis of your Azure Tenant configuration, policies, best practices, and compliance. A higher number indicates that more security practices and policies are in place, therefor reducing the security risk for a company.
Click into the Secure Score on the Remotely dashboard for a break-down of your Secure Score across your organization's Identities, Devices and Apps, as well as other information on Data Compliance.
Your Exposure Score reflects how vulnerable your organization is to cybersecurity threats — the probability, scope, and severity. This composite metric comes from Microsoft and is derived using global / real time sensors and threat analytics. While somewhat aspirational = the lower the score, the less vulnerable your organization tends to be to endpoint / cyber incident. Nothing is fool proof except effort.
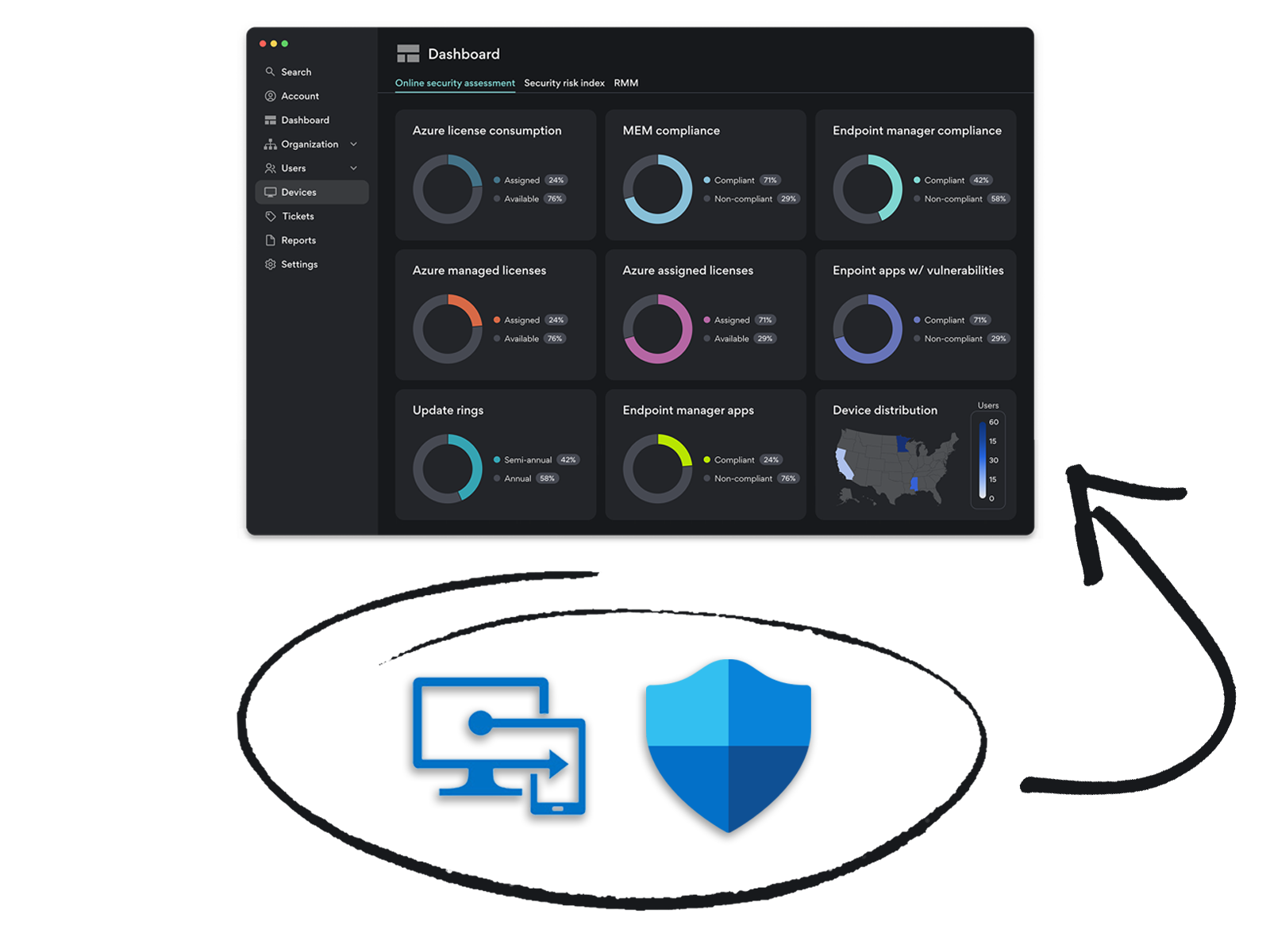
Endpoint Management Compliance checks the devices on your network against your Endpoint Manager Baseline to determine if they meet your compliance standards or not. An incredible number of companies own Endpoint Manager / Intune, and our hope is to enable more successful outcomes.
In Remotely, you have complete visibility into how many devices on your network are compliant — and how many aren't.
Microsoft Office is foundational for most organizations. Stop overpaying for licenses you don't need, or underusing licenses you're already paying for.
Azure Active Directory gives organizations new introspection and management into application lifecycle management - Remotely captures all of this and more.
Remotely shows you:
- The current number of Azure Managed Licenses, including those that are ordered or registered through marketplaces like Azure Marketplace
- Your number of Azure licenses that have been assigned
- Your number of unassigned Azure licenses
- Services your users are Using
Zero-day exploits take advantage of slow responses and poor preparation. A critical datapoint in maintaining the security posture of a company is ensuring appropriate patch management and update policies are in place and adhered to.
Remote users make staying up to date more difficult as most schedules are no longer 9-5.
Microsoft enables this functionality though Microsoft Endpoint Manager with a feature called Update Rings.
It's vital for organizations to know which devices are behind on updates, and therefore more susceptible to unique bugs and vulnerabilities. With Remotely, you have real-time visibility into your org's update cadence policy, and posture and what's falling behind.
Hacker's only need to get lucky once - security professionals need to be on guard always. Untrusted networks and lack of security presents a significant risk to the organization.
Where are the users on your network located? How certain are you about their location accuracy?
With Device Geolocation you have complete visibility into the locations of your distributed teams' devices down to the meter.
Endpoint Manager Discovered Apps in Remotely not only show you a complete inventory of the apps on your network's devices, but also who owns them.
What has been installed? What has been removed? Who has what version of what?
Remotely inherits organizational and group structure out of Azure Active Directory, allowing us to fully map your Endpoint Manager Discovered apps to their owners for you to easily drill down into the data.
Don't waste resources keeping track of every single NIST CVE and determining how they may affect your organization. With Remotely, you can see in real-time the percentages of installed software on your network with and without vulnerabilities.
Which users, which versions, which CVE are one click away.
Click into the Remotely M365 Defender software Inventory and Weaknesses modules to drill down into:
- M65 Defender Software Inventory
- Exposed Weaknesses and Device Count
- Which users have the susceptible apps on their devices
- Vulnerability/CVE alert name
- Affected product
- Product Vendor
- Product Version
- Weakness Severity
- Recommendations for fixes
Time to value in seconds.
Unlike legacy on-prem solutions.
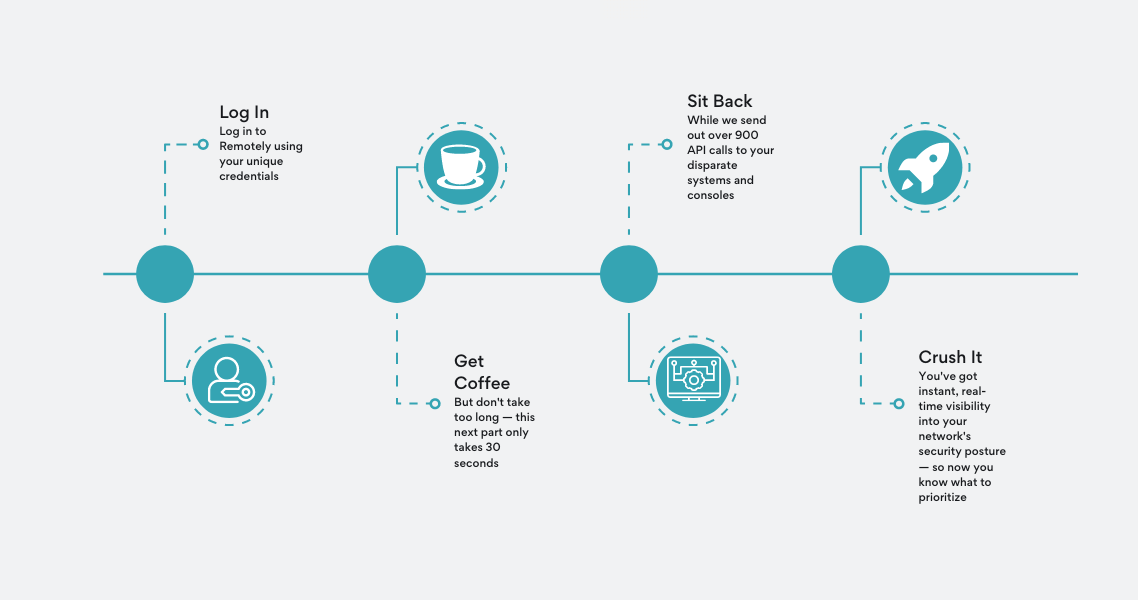
Saying we can identify every vulnerability in your network is a bold claim.
But we can.
This is how we do it.
Remotely connects to your Azure tenant (with the required security permissions) and from there we make over 950+ API calls across Microsoft GraphAPI, Azure Active Directory, MS Intune, MS Defender for Endpoints (and a few other places).
We get a ton of information on each machine as well as user identity that has presented itself on your network for authentication. The age, location, application inventory, update and patching policies, and compliance status are instantly illuminated.
This full inventory of information and application data is checked against the NIST CVE database before posting the data to reveal the scope, severity, and probability of a cyber incident.
From there, we built the coolest and most powerful PowerShell agent that is deployed on your Windows Endpoints. This allows us to gather virtually any metric, measurement, or data available to the operating system, and bring it back into Remotely.
All of this information is stored in your privately provisioned Remotely instance - isolated from all in/outbound traffic and other deployments. This is YOUR data. And that's how it's done.
.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)
