IT admins can define rules and settings inside MEM that managed devices must meet to be marked compliant. This is where compliance policies come into play. Furthermore, IT admins can leverage Conditional Access policies to use the results of your managed device compliance to determine which devices can access your organization’s resources. To create a new policy in Microsoft Endpoint Manager, admins will want to click on Devices in the left nav pane, then click Compliance policies, then Create Policy. Select the platform you want the compliance policy to apply to, in our case with a mixture of Windows 10 and Windows 11 devices, I will select Windows 10 and later. Give your compliance policy a descriptive name to help other admins understand at a quick glance what the compliance policy is meant to be doing and click Next. The compliance settings tab is where you will choose the settings to be applied to the managed devices from a compliance standpoint. You can configure things such as minimum OS requirements, require Bitlocker encryption, require a specific password policy, and more. If I can offer any advice here on the architecture of your organization’s device compliance policies, I recommend separating multiple compliance policies. This makes it easier to troubleshoot any possible issues with the compliance policy. Separating out compliance policies also offers a more organized, cleaner feel to the policies. Combining multiple compliance standards under a single policy may be quicker, but it can save time when troubleshooting or looking to make changes to a compliance standard in the future.
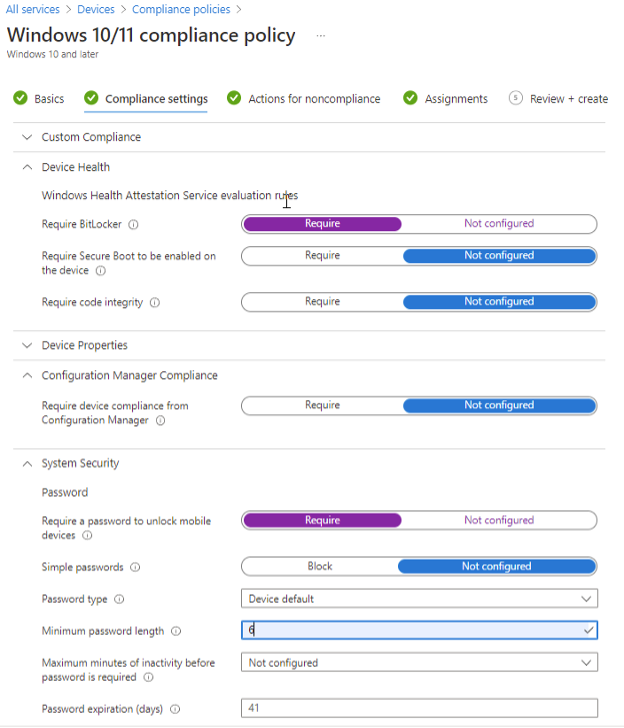
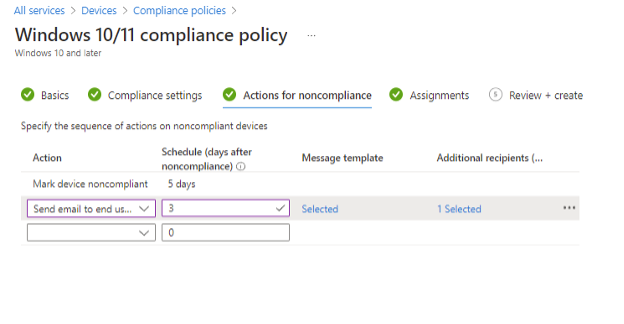
Under actions for noncompliance, you can configure the actions to take on users/devices that do not meet the requirements of the compliance policy as well as define how many days of non-compliance before the actions are taken. Think of this as a grace period. In our case, we are going to send a custom email to the user notifying them that their device does not meet the compliance requirements with an additional recipient of a lead IT administrator who can work with the user to get the device compliant.
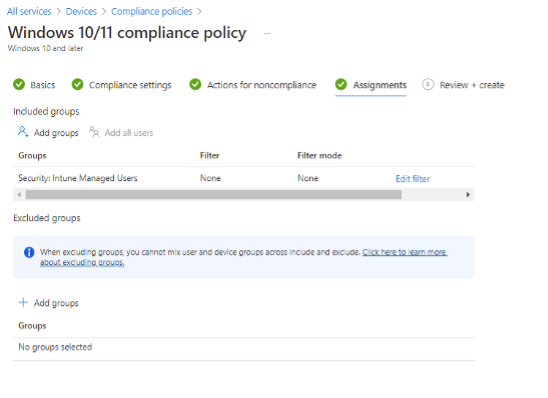
Next, determining whether to apply a compliance policy at the device level or user level can always be a challenging question at first. While there is no definitive answer, IT admins should ask themselves “What am I looking to accomplish? What type of policy am I looking to define?” A good rule of thumb when configuring compliance policies in MEM is to apply the policies to the User group. When you assign compliance policies to devices you will find there to be multiple compliance results for every device; the built-in policy, the “system account”, and the user signing into the device will all receive a compliance status. Unfortunately, this can lead to errors in compliance reporting by MEM for the different accounts and create massive confusion. Save yourself the headache and apply compliance policies to users.
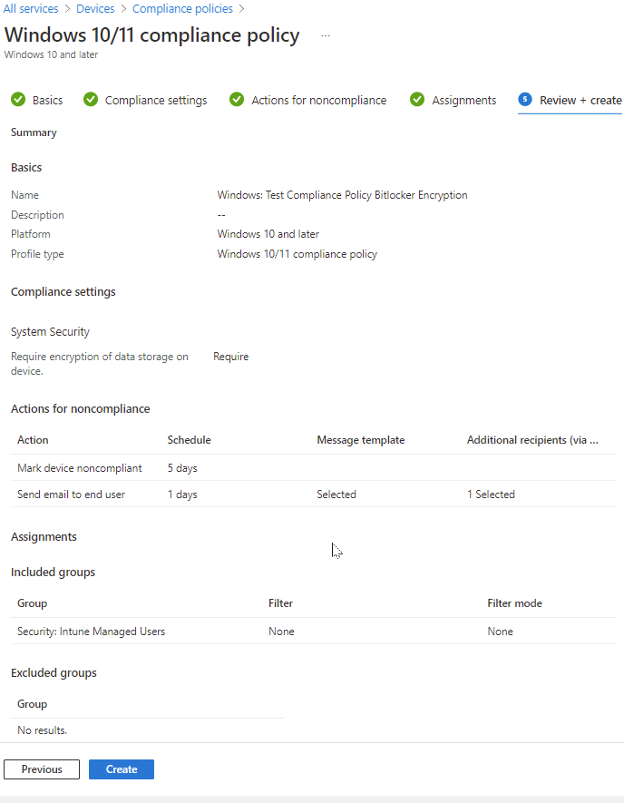
The final stage of creating a compliance policy in MEM is to review your configurations and assignments to ensure you have configured the right policy and assigned it appropriately. When ready, click Create. Note that with many configurations in Azure, there is replication time involved for the policies to reach your targeted endpoints. You will not see results right away. I have made policy changes in this portal and it is not abnormal for 24 hours to pass before updated changes are taken into effect.
No Comments Yet
Let us know what you think