Introducing: The Remote Risk Dashboard
by Tyler Rohrer on November 17, 2022
A dashboard should be intuitive. A dashboard should not be an eye chart. A dashboard should unify and present disparate information in a consumable way. A dashboard should display value, not merely information. Too much noise, and no signal and we will turn the channel, close the tab. We all make decisions with imperfect information...what if that did not need to be the case? With a full spectrum of information we can model possible outcomes. This is why we use dashboards - for outcomes of value. What do we value most? Many would agree TIME wins this category every time. A dashboard that saves time would be amazing. Let me show you what we built to save you time.
With so many of our team members engaging with our organizations in remote and hybrid models - truly working from anywhere as digital nomads - keeping them secure and supported takes a LOT of time. We all have had a tool belt of kit, solutions, consoles, scripts, or apps that helped us nudge our days forward. There is a certain overhead that comes with being understaffed, and over tooled.
Trying to find the root cause of RISK that exposes them or your company to cyber threats would take an eternity if we had to continuously collect and correlate measurements from all our systems.... Until now.
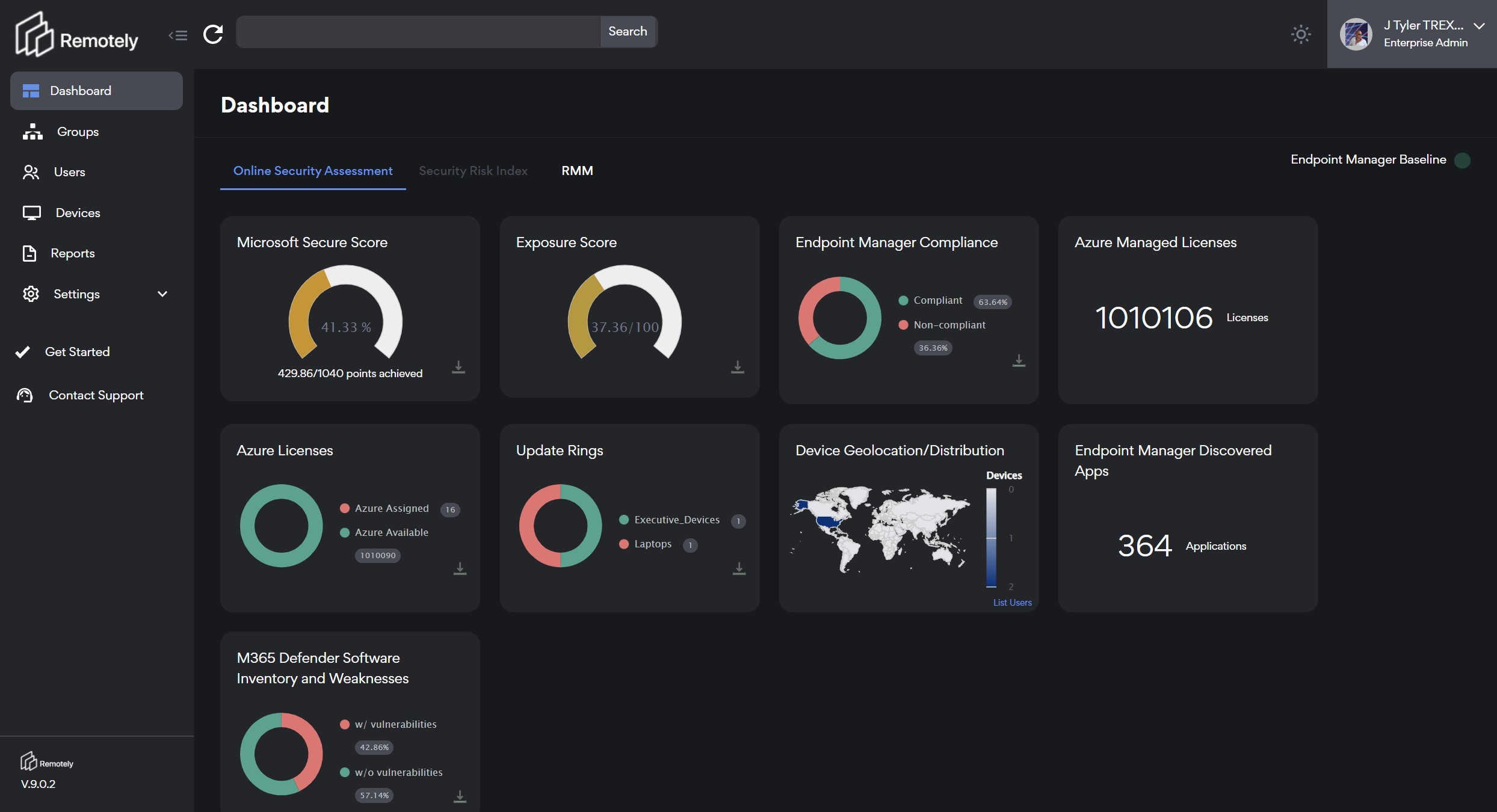
We endeavored to build a dashboard that exposes Remote Risk. RemotelyRMM is a Risk Management and Monitoring Service that runs in Docker Containers in Azure (or a rack near you). We sought to unify both the cloud centric and end user / endpoint solutions that gave you information for decision support into one hyper converged console.
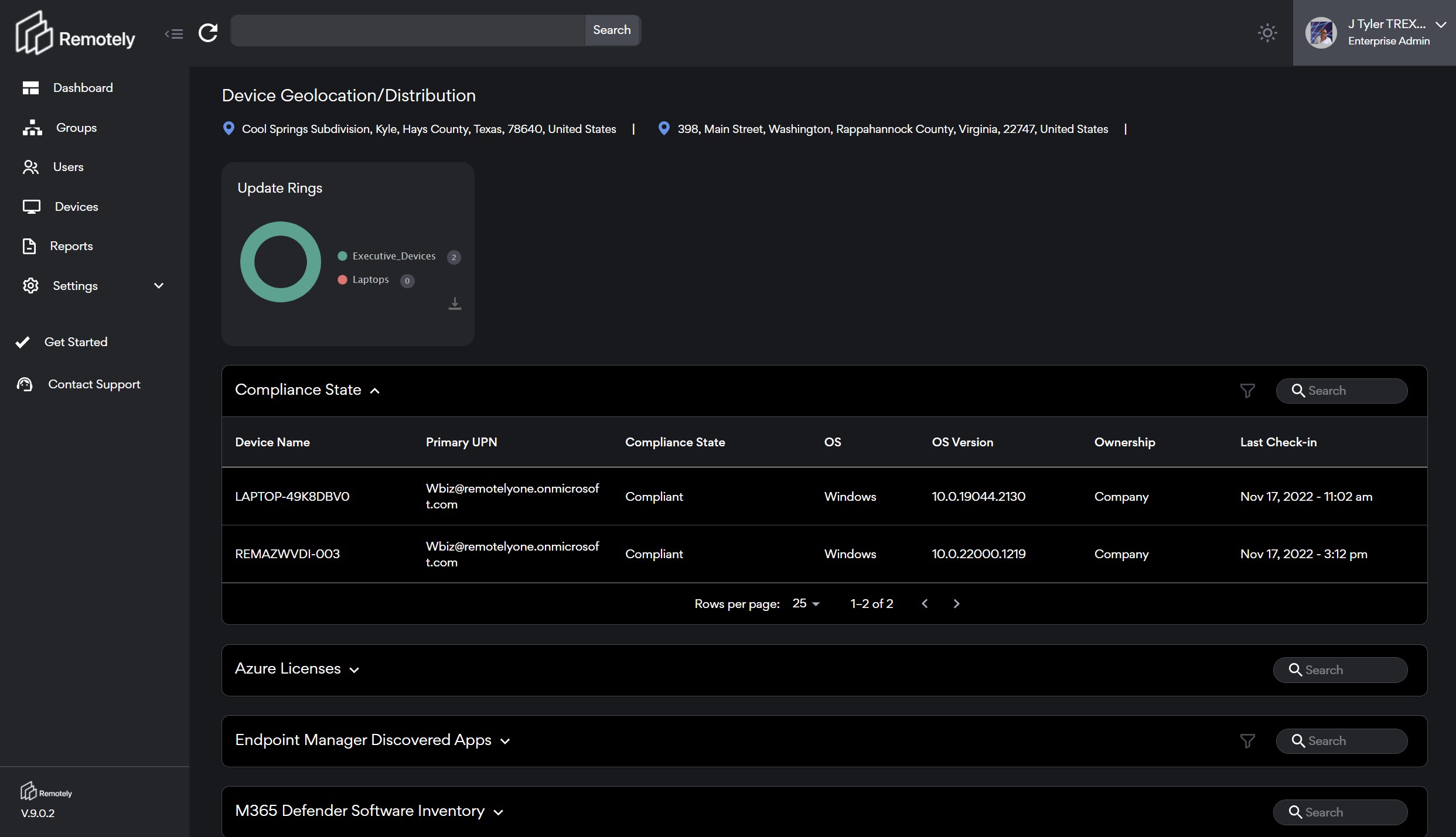
We "turn on the lights" in the dark room of remote work. Every Active Directory Group within your organization is illuminated on login. The dashboard is aspirational from the standpoint that we show you your Microsoft Secure Score which is a measure of your organizations security posture vs. your peer group and Microsoft best practices. We continue with your organizations Exposure Score, licensing ownership and utilization, device enrollment, compliance, updates, geolocation, applications, and vulnerabilities.
Each one of these domains presents an incredible opportunity for improvement. We can strive to increase our Secure Scores, Lower our Exposure, Optimize our Licensing, Drive Compliance and Device Enrollment, Validate User Locations, Inventory all of our Applications, and Expose your Application Vulnerabilities.
Next, we deploy our PowerShell agent to endpoints and the magic continues. Using PowerShell we have access to virtually any metric needed or imagined from every endpoint on your network (Windows today, Mac, Chromebooks, Linux soon). In our dashboard we toggle over to our Endpoint Tab and now we see unified metrics from across EVERY group in your company. Users, devices, performance, applications, data, networks, firewalls, policies, storage, encryption, patching, services and more are simply presented with a few clicks to complexity.
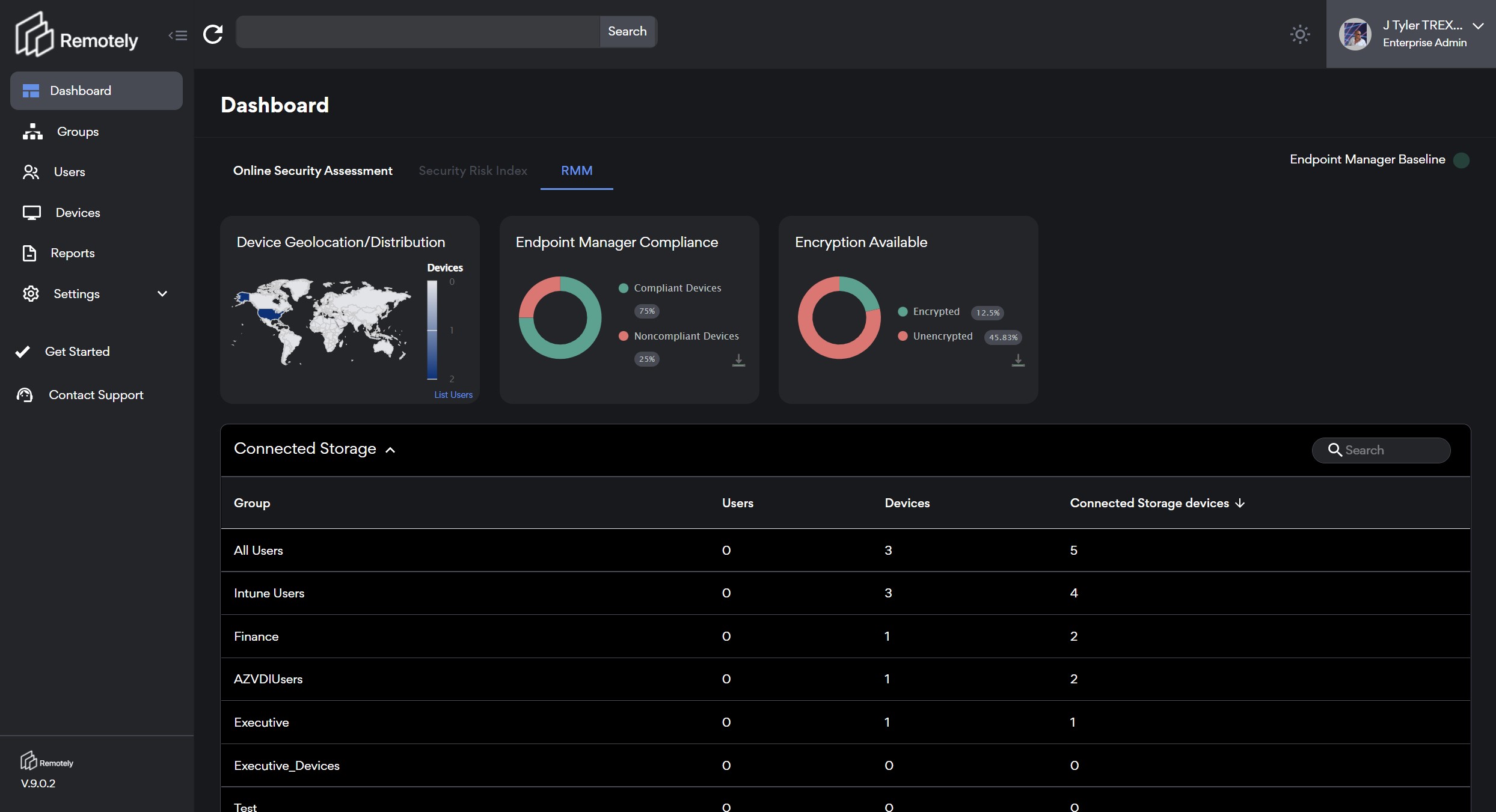
A large part of decision support is providing the value of scoring or prioritization. The ability to look across your distributed user base and quickly select and analyze groups for deeper inspection is critical. It is highly likely that given the different systems, applications, and locations of your end users risk and security concerns will present themselves in asymmetrical ways. Often locations, departments, or even machine types will be the "group" you need to focus on.
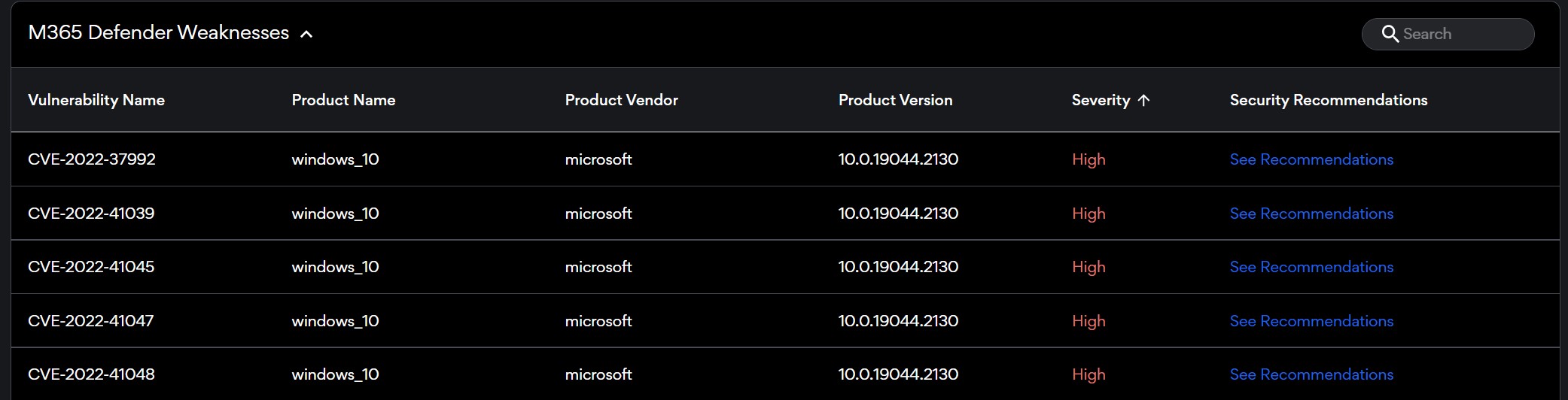
We all are faced with the increased cost and complexity of distributed workers in different ways given our businesses. For that reason we speak about groups in two ways - logical groups (sales, finance, Illinois), and observed groups (out of date patches, installed application(s), encryption status. There are a number of projects for risk reduction in following a well implemented Risk Management Framework for both logical and observed groups.
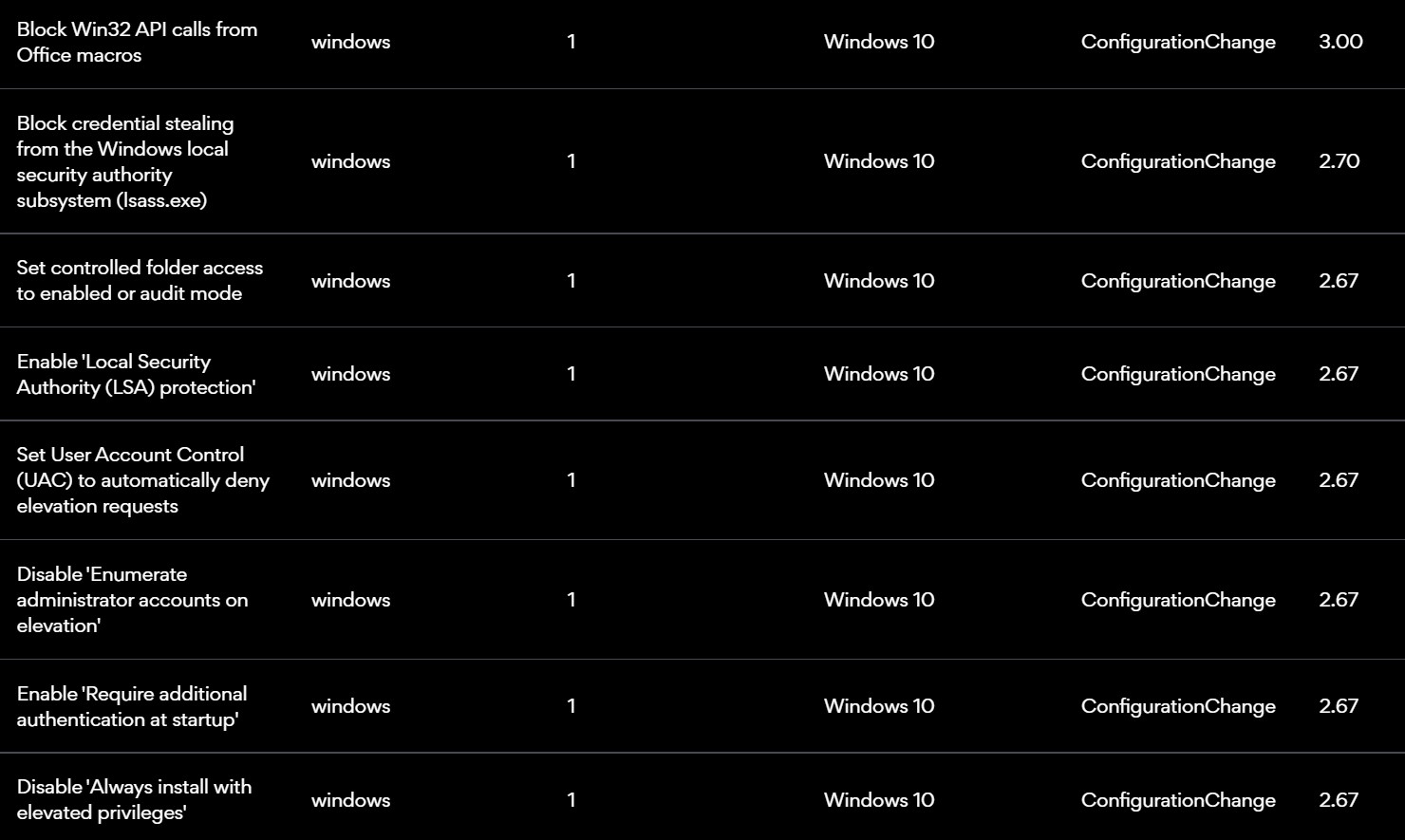
If we use our aspirational dashboard to help guide our projects we are fortunate to inherit the best practices security and exposure reduction recommendations from Microsoft. The same can be done for our global application inventories by taking the steps recommended to harden our systems and apps.
Remotely's taxonomy flows from Enterprise to Group to User to Device to App etc. As such we know that a large part of the Modern Workplace is the use of cloud based, session based, or virtual desktops as a service. As such, many users will be on many machines, with different applications, profiles, data, and perhaps policies applied. Instead of trying to map policies to static ideals - we are seeing a large number of companies adapting security policies to fit the way users work.
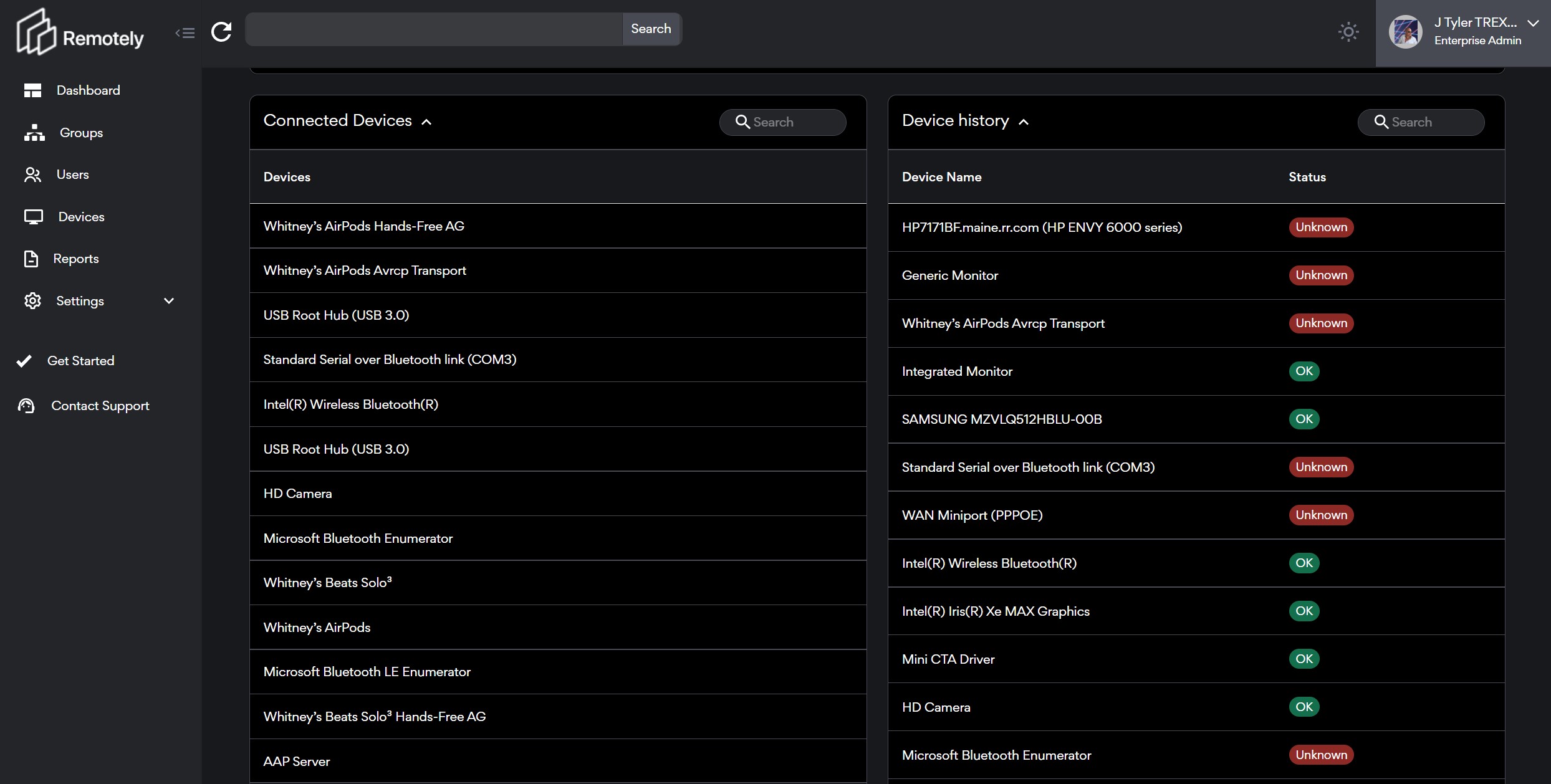
With users using multiple devices we must acknowledge that endpoint complexity adds risk to our security posture. Every exposed port, signal, external device, or driver we bring into the environment adds a vector of possible exploit. We believe it is critical to have full visibility into each and every one of these aspects. As we know today's modern peripherals often come with "apps" either for the desktop or mobile device and knowing what our users have installed is a key part of helping secure and support them.
There are hours of exploration we could take you on as it relates to the RemotelyRMM dashboard. We invite you to sign up for a DEMO and get your own credentials to take a TRIAL RUN. We have taken great care to create getting started documents and consultants delivery guides to assist you in both strategizing on implementing Risk Management Frameworks for your End Users or to work with your customers or managed service providers to add RemotelyRMM to your solution stack.
In our next blog we will dive into Endpoint Metrics, Performance Observations, and Considerations for Next Generation Workspaces. Until then feel free to Subscribe.
Tyler T.Rex Rohrer
November 2022
Add some fun, compelling content here
- Cyber Security (16)
- Security (15)
- Azure (10)
- Cyberattack (10)
- IT Operations Management (10)
- Remote Monitoring and Management (10)
- AIP (9)
- IT Strategy (9)
- Remote Work (9)
- Asset Management (7)
- IT Operations (6)
- Asset Inventory (5)
- Reliability (5)
- Remotely Interesting (5)
- Risk Management Framework (5)
- Azure Migration (4)
- Microsoft Secure Score (4)
- Office 365 (4)
- Security Risk Index (4)
- Customer Success (3)
- GRC (3)
- Risk Dashboard (3)
- Support (3)
- Powershell (2)
- First Steps (1)
- Migrate (1)
- System Requirements (1)
- Virtual Machine (1)
- Zero Trust (1)
- August 1, 2023 (1)
- July 1, 2023 (2)
- May 1, 2023 (1)
- March 1, 2023 (2)
- February 1, 2023 (1)
- January 1, 2023 (1)
- December 1, 2022 (2)
- November 1, 2022 (2)
- October 1, 2022 (1)
- September 1, 2022 (2)
- August 1, 2022 (1)
- July 1, 2022 (1)
- June 1, 2022 (2)
- May 1, 2022 (4)
- April 1, 2022 (3)
- March 1, 2022 (2)
- February 1, 2022 (2)
- January 1, 2022 (1)
- December 1, 2021 (4)
- November 1, 2021 (1)
- October 1, 2021 (1)
.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)


No Comments Yet
Let us know what you think