Risk Management Frameworks for Enterprise Endpoints & Distributed Teams: Security for the New Normal
- Chapter I: What is Risk Management Framework Software?
- Chapter II: Benefits of RMF software
- Chapter III: How RMF Software Is Used
- Chapter IV: The Value Add of RMF on Azure
- Chapter V: Common RMF Functionality
- Chapter VI Benefits of RMF Software
- Chapter VII Assessing RMF Software
- Chapter VIII Conclusion
What is RMF Software?

Risk Management Frameworks as they relate to the security of technical systems have historically and importantly focused on data center and operational technology. For decades those were our most exposed attack vectors. Very little work has been done to date to extend these frameworks of risk reduction out and across our populations of end users. With the explosion in popularity in Work From Anywhere, Remote Work, our distributed teams are under incredible stress.
For quite some time our user populations have felt that working in flexible locations using mobile technologies allowed them to be their most productive. Overnight what was previously a luxury or occasionally the case became the new corporate standard. With our users and teams that supported them scattered to the wind our costs, efforts, and risks soared. While there are meaningful conversations surrounding return to office initiatives, we suspect a vast majority will remain and prefer working Remotely.
The concept of Risk Management Frameworks began with the United States Department of Defense together with the Department of Commerce in 2012 and has been revised and branched to other domains since inception. The 183 page document known at NIST 800-37 is a wonderful conceptual starting point for security practitioners or end user computing system administrators looking to secure remote workers, endpoints, and data.
One primary challenge is that our reliable system support models, technology solutions, trusted workflows, and safety measures now appear almost meaningless in the face of the security fronts we must contend with. Work has changed. The office has changed. So too have the patterns and tech stack available to us. We are now being compelled to face, contend, correct, reimagine, and redeploy decades of great ideas. This is a change in basic assumptions that touches end user computing more than any other domain.
Legacy on prem Monitoring, Management, Reporting and Alerting software (RMM Solutions) coupled with integrations into Information Technology Service Management (ITSM) solutions like ServiceNow, Microsoft Intune, and Helpdesk platforms used to be our line in the sand.
Fortunately, we have some incredible lessons learned in our decade plus pursuit to virtualize the desktop that we can apply to this new work and technology model. We also have tried and true adoption enablement and onboarding practices that have been developed over the years.
For those organizations that are determined to push back against Ransomware, Cybercrime, Security Costs, Cyber Insurance, and other derivative consequences of the new normal- adopting a risk management framework specifically around endpoints and distributed teams can be crucial.
Additionally, the observations surfaced, and metrics collected can be of incredible use to other groups within the organization focused on workplace modernization or regulatory compliance for example. endpoints and distributed teams.
While there are individual steps that can be taken by each user to find and manage risk, there are also group steps that can be taken. Both are of equal importance. Our hope is that supplying a framework to approach the domain of remote user risk management systems and runbooks can be developed by each of us for our use cases.
The goal of most tools used by IT departments in and across the modern enterprise is to ensure that remotely connected IT assets are standardized, operating according to existing standards, and performing optimally. Better said -does the technology provisioned to the end user allow them to do the job they are tasked with doing? Legacy RMM tools tend to include features that ensure IT professionals can allocate tasks, automate maintenance jobs, and track issues seamlessly are increasing in popularity as we see a stampede of hybrid, work from home, and work from anywhere shifts.
The wrong systems, or lack of RMM systems that are in line with your business goals, can cause immediate friction and loss of user experience as we have shared in our "What is RMM Software" guide .
With the right support, security, and remote monitoring, businesses can easily improve their network performance, network security and increase end user productivity. What is the purpose of a well performing PC that is not secure? It is only capable of infecting and compromising its peer group faster. This is to be avoided. We must endeavor to find solutions that weave SECURITY with RMM.
This is where the concept of RMF for Enterprise Endpoints was born. The vision was to take a really good start in on prem RMM solutions and create an implementation focused as much on End User Productivity and Risk Reduction as it was with basic system performance.
While Remotely is perhaps the first Enterprise End User Risk Management Framework yet developed and offered as a Cloud Native SaaS Subscription Service - the core functional areas included, per the NIST 800-37 RMF Framework:
- Prepare your RMF Project
- Assess your remote risk(s)
- Score / Prioritize the Risk(s)
- Address / Remediate / Avoid
- Monitor to Validate
The goal of this document is to share a model for reducing risk and increasing the productivity of our remote users, staff, and budgets.
While nothing is industry or vertical specific, we expect to share future documents surrounding highly regulated industries, government agencies, and global scale enterprises. As this is an open framework, the contribution of readers is highly desirable.
New remote risks for enterprises
The need for enterprises to protect and monitor their remote devices is accelerating.
use personal devices to access company networks
use work emails and passwords to access consumer networks
most feared risk: cybercrime, IT failure, and data breaches
How Companies Benefit from Risk Management Frameworks

There are an almost innumerable number of RISK headwinds facing modern enterprise IT departments and security practitioners as we contend with such a large population of end users in volatile locations. In fact, many CISO's, CISSP's, and security team members tell us that major factors they manage to daily are:
- Increase in Cyber Crime Insurance Premiums
- Increase in Regulatory Fees/Fines/Compliance costs
- Real costs of Ransomware, User Downtime, Productivity Loss
- Variety, Volume, and Volatility of End User Behavior creating risk
Risk Management Frameworks, while not new, have rarely been applied out and across our massive populations of remote end users. Up until this point – most users tended to log hours in primary office locations.
This document will try to define a method for risk management frameworks focused on enterprise end users and endpoints. While many of the workflows and processes that will be discussed in this document can be carried out manually, our examples will use RemotelyRMM to aid in the assessment, scoring, prioritization, validation, and ongoing monitoring of the environment.
Remotely strives to create a common dialogue and definition around Enterprise Endpoint Risk Management Frameworks so that a community dialogue can ensue. Creating systems and workflows that can identify risk, mitigate the impact of risk, recover from risk incidents, and prevent future occurrences is paramount.
With most of our end users working from a variety of locations, information and context about how, where, and when they work is crucial. With distance being one of the primary impediments to our efforts in trying to secure and promote their productivity – information and understanding are even more important to our organizations. It has been said that we cannot manage what we cannot measure.
A lack of deep visibility can result in less-than-optimal outcomes. Inaccurate information and a clear awareness of the “current state” of technology makes it ever more challenging to manage out of that state to a more desired one. Adding to the complexity is that our teams all use separate consoles historically to accomplish the tasks in supporting our end users. very few of these solutions share information in a correlated way across teams. one aspect we will speak about at length in this document is the unification of system information. 1 source of truth for all teams.
The greatest challenge for many risk and security experts isn’t always the known issue that presents itself across your user base, but rather the unknown issue that has not yet even been discovered, an exploit not yet run.
Our thesis is that massive data and a shortened feedback loops in one cloud console will cut IT Team Member Effort, reduce RISK to the organization and enlist everyone into the security mission. When all team members can be responsive to end user needs and effective in their ability to mitigate risk the company will be in its strongest security posture.
An enterprise endpoint risk management framework for distributed teams is a powerful instrument that is surprisingly simple to begin and implement when using a cloud solution such at RemotelyRMM.
Visibility and Observability were the key words used over and over in explaining the primary challenge facing security experts and system administrators. You cannot manage what you cannot measure (or cannot see).
One of the first benefits of an RMF implementation, and using a simple solution like RemotelyRMM is the ability to assess the security posture of each and every user, device, application, and server on the network.
We must be aware how much larger and more porous our distributed network now is. The configuration, usage patterns, location, and role based access all go into a knowable security posture or stance. Applications, devices, or drivers that have known exploits, security flaws, or present risks must be accounted for in order to be avoided or overcome.
Now that you have visibility into missing updates, patches, antivirus routines, device configurations, firewall policies, or a lack thereof - we can begin to detect, avoid, remove, or work around the observed risk(s).
Today - most organizations have 10 to 20 disparate consoles they use for Updates, Patching, Licensing, Geo Location, Applications, Windows Logs, Network Status, Storage Management, Encryption, and more. The costs of collaboration sky rockets between teams and tasks when we need a central repository of the data.
- Human Error
- Complex & Non Correlated
- Time Consuming
- Expensive
Using one "source of truth" in implementing your Risk Management Framework is highly recommended to avoid the lack of productivity too many tools brings.
We want to create reliable computer systems out of intrinsically unreliable components (including our end users ;). While easier said than done - we have two routes. Build to a spec, then contend with the errors we confront as systems are rolled out...or, observe our system in production, and pivot our strategies to fit these use cases.
If we can automate the mundane tasks of data collection and spreadsheet cutting and pasting, we allow the IT staff to focus on higher priority projects. There are certain realities like systems or applications failing forgotten passwords and inconsistent networks and our goal should be to design around them when possible remediate when we can. However, legacy RMM use cases tend to be "$100" problems like the need for more memory, or help with an application. RMF solutions on the other hand have the ability to bring into focus "$1 million" problems like cyber insurance rate mitigation, breach avoidance, or lack of productivity to large numbers of users, staff, or budget line items as the result of a risk incident.
Remote Management and Monitoring software solutions are a great way to reduce the time it takes to remediate tickets by 50-70% - Especially in the new distributed environment we find ourselves in these days where distance in proximity works against us.
However, the sheer volume of distributed users compels us to move from a REACTIVE MODE to a PROACTIVE MODE. We could spend our days in fire drills triaging and fixing broken and compromised systems. Or, we could approach Risk Management proactively - using the steps of the framework above to avoid, eliminate, or re-architect our solutions.
Some of the more progressive companies we speak with share that efficiencies and response times have been hyper optimized as they've begun to use cloud solutions specifically Microsoft Azure. To that end there is tremendous information available in and across the different Microsoft solutions we use like Microsoft Intune, Microsoft Endpoint Manager, Microsoft Sentinel, Microsoft Defender for Endpoints, Purview, Azure Active Directory, as well as available via Microsoft Graph API.
Furthermore - no solution is complete without an ability to inspect the edge. For this reason RemotelyRMM selected to build our agent software in PowerShell.
End users have long posed risk to our organizations and even more so with the rapid proliferation of mobile computing and portable devices. Over the years several technologies have been successfully deployed to aid the occasional remote user use case from a provisioning security and support perspective. No one expected we would have several orders of magnitude more complexity at the edge. While a significant driver in many end user computing solutions is security, adoption did not take place at a pace sufficient to react to such a rapid shift in workstyles.
Solutions like desktop as a service (DaaS) or virtual desktop infrastructure (VDI), even legacy remoting technologies and server-based computing (SBC) along with cloud-based technologies and hyperconverged platforms offer great promise for many use cases. Whether it be application contention or the need for secure remote access – secure and centralized management are great benefits. The use of thinner and more secure operating systems at the edge also increases our security posture.
When the work from home / work from anywhere box was opened in 2020 we unfortunately did not have time or preparation to extend those architectures to all our newly distributed team members. Customers report the primary architecture they deployed was a laptop provisioned from a big box retailer typically with local admin rights and VPN software that's rarely used. Exposure today lies in and around those users on laptops on and off trusted networks with asynchronous and nonlinear workflows. Traditionally the close interconnection and inter use of personal devices for corporate work only adds an added layer of risk that needs to be addressed.
When it comes to end user computing several methodologies have proven to be tried and true and such is the case here. We can look back to the adoption of antivirus and antimalware software to efforts in and around virtualization of the desktop user profile and applications all the way out and across cloud-based solutions and services. The goal has very often been the same to supply reliable computer systems out of intrinsically unreliable parts that keep our staff, our budgets and our users productive.
With our teams now on untrusted and unreliable networks always, doing unknown things with local administrator rights...visibility counts more than ever as we've mentioned. said another way to truly see secure and support their productivity we need access to as many data streams metrics and measurements as possible from the edge all the way to the cloud and our data centers.
To create a truly effective risk management framework we should try to capture as many measurements' metrics and data streams as possible. Furthermore, what is increasingly important are not just the consumption metrics of CPU memory disk and network activity but also the security compliance configuration and encryption status of our endpoints.
We also need to consider the security exposure compliance and update cadences our different users and groups are enrolled in. obviously adherence to the policies we deploy is also critical as often breaches and incidents have been proven to relate to lack of fidelity to policy.
Next - how to sign up, log in, and blow minds.
Supporting content
How can RMF Software be Used?

While software focused specifically on Risk Management Frameworks has not existed previously, there are a number of features and functionality that our teams will require - born in large part out of the need to consolidate our legacy tools as well as enjoy previously unavailable data sets.
As with any technology project one should begin with a firm understanding of the problem or problem set that you are trying to solve for. in this case we will assume the context is the establishment of a risk management f framework for your remote workers. Furthermore, we are also interested in conducting both a wide scale assessment to gather as much information as possible as well as establishing baselines for observed user behavior and system performance as well as fidelity to policy and standards.
Our methodology focuses on the use of an assessment that looks out and across Two primary domains the first is the users Microsoft cloud identity. We are interested in their enrollment in device management, the security of their applications, their identity, their devices and their data. We have access to amazing threat analytics through Microsoft and exposure score is a meaningful measurement we want to collect. We also see licensing
With this information several potential project types might ensue all of which can be considered part of a risk management framework. Your preparation and choice of desired outcomes will aid you in using the most important data and findings for your project.
- Incident Response & Threat Hunting (risk not code)
- Workforce Modernization
- Risk Mitigation / Security
- Strategic / Competitive Plans
Incident Response & Threat Hunting
Incident response projects will use the risk management framework data and findings from RemotelyRMM to better understand the root cause as well as areas of improvement in process product or architecture. In this domain we are specifically interested in finding, isolating, removing, then monitoring the environment to ensure the risk has been removed.
There are a ton of real time incident response and threat hunting solutions on the market, including those from Microsoft. These solutions can both track and stop malware, viruses, exploits, threats, bad actors, and more – and serve as a repository for information and learning on past events. While these solutions are amazing in their current state, they do miss the individual RISK many users, devices, configurations, or use patterns can pose to the organization. Furthermore, nothing can replace poor policy adherence, device enrollment, or data protection strategies.
Workforce modernization focuses on the use of advanced virtualization and cloud-based technologies to change the architecture in how we deliver applications data document services and run times to our end users. One solution with tremendous momentum happens to be desktop as a service (DaaS). in this model the operating system user data including documents settings applications and profiles all live in the cloud and are accessed from a host of potential devices at the edge. These devices can range from existing fat clients' laptops web browsers specific client software as well as tablets and phones for some use cases
Workforce Modernization
Workforce modernization practitioners benefit in two primary areas using solutions like RemotelyRMM. primarily are the configuration and consumption patterns across your end users. Although we may change the architecture deployed to our distributed teams very often their daily work patterns will remain the same and therefore, we can use a baseline of their current activity to plan future needs. Image design, antivirus software corporate applications and access to company resources are all elements we can observe today to help us plan modern workforces and solutions tomorrow. We can begin to see cost visibility in terms of the resources that will be required to deliver a similar user experience and the cost of the infrastructure needed to do so.
Additionally, we can use the metrics and measurements to increase Security posture and lower risk exposure. An astute observation of the users' group's locations or use cases that are creating friction from a security compliance device enrollment perspective can assist in prioritizing user groups for any project. IF there are risky applications with vulnerabilities or locations or missing configurations these can all be figured into our architectural decisions and management controls.
Risk Management
Risk mitigation will be the primary focus of this document as it relates to the elements we believe and conclude are large in reducing the attack surface of any distributed team of size. This document will try to define those elements that reasonably contribute to or reduce the risk of an endpoint or end user. As no organization, agency or enterprise is identical, we trust that the suggestions serve as a baseline from which you are specific context and priorities can be realized.
We will focus on several primary categories.
- Secure Score / Exposure Score
- Antivirus / Anti Malware / Operating System State
- Compliance: Updates, Patching, Encryption, Usage of Corp Resources, Applied Policies
- Licensing: do you own, maintain, secure, and pay for resources
- Location: are users where they need to be, using what they should be
- Applications: in an effort to get the job done, or evade IT
- Environmental Vulnerabilities: apps, networks, devices, drivers, etc
Microsoft assesses, measures, and calculates a Secure Score for every user on your network based on their Devices, Applications, Identities, and Data based. This score measures the extent to which risk has been offset by taking recommended preventative measures. While no metric is perfect – this aspirational score shows both the gap in users versus “best practices” - as well serves as a scorecard where recommendations and their impact to overall score is used.
RemotelyRMM pulls all this information into our database as we believe it, together with a host of added data streams, is critical to have a multidimensional view of your risk exposure. As the Secure Score includes several elements – we can click in on each for deeper understanding of risk.
An organization's Microsoft Exposure Score is a measure of the vulnerability to cyber threats across your end points. The likelihood, scope, and impact of an event can often be mitigated through security steps and policies. Remotely uses Exposure Score metrics in our database to calculate other composite metrics and to help in scoring and prioritizing risk vectors. We have made great investments in and across our antivirus and antimalware solutions. For this reason, making sure our end users and endpoints have the latest versions definitions and updates against zero-day exploits is critical. Those users who are habitually not up to date with patches can be isolated for further management. This leads us to overall patch, update cadences. There is often a great deal of effort wasted in designing and deploying security solutions, updates, patches, scripts, policies and more if our users circumvent them or ignore them. tasks as simple as pending reboots can make the difference between secure and at-risk systems and networks.
Remotely collects all this information so you can quickly see which Groups, Users, Devices, or Regions are putting themselves or the organization at risk. Additionally, unlike traditional solutions we also collect full endpoint information as it relates to the utilization of provisioned corporate laptops and resources. We are also interested in the performance and security of the networks remote team members are using. security and encryption is only as strong as the weakest link.
Licensing at scale can be a perplexing task. Microsoft Azure Active Directory gives you the unique ability to manage applications. With a robust API we are able to collect all of the licensing and assignment information as well as the individual services an individual may be using. We often see under provisioned or over provisioned resources which can be opportunities for not only cost savings but attack surface reduction as well as team effort.
We have found that work from anywhere truly means that. The variety and volume of networks devices and locations users have begun to use daily has exploded in number. Often time tasks are completed with a combination of smart phone personal computer cloud resource and virtual applications. it is important to all of our assessment activities and analysis to know where our distributed team members are working from.
Not only will this assist us in reducing security risks and setting new policies and rules, it will also help us and potentially architectures moving forward. Users that access corporate resources from several locations increase the complexity however not the need for measurement. Remotely captures these disparate sessions and provides actionable data on each at incredibly detailed levels.
We believe users do two fundamental things which is create and consume content... and applications are what they used to do that. These programs together with the system services and processes that make them work are also and obfuscated root into our corporate networks four bad actors. The National Institute for standards and technology NIST maintains a real-time database of known application vulnerabilities known as CVEs. These vulnerabilities can have a direct and negative impact on an organization and range from critical severe to low level.
Remotely not only collects an entire inventory of all applications installed and used across all devices we also display these NIST CVE vulnerabilities together with steps for remediation and impact to risk improvement based on steps taken. We need to remember that these days some applications do synchronization of data or settings across devices and while this may appear useful and truly does help productivity it is also a way for penetration.
How, where, when, and on what device users log into also plays a huge role in their potential risk and its impact to an organization. What devices or peripherals are they plugging in? What drivers or software are they installing for home printers? What applications have they removed or are not using? Anything in the Windows Log Files we might want to see? Environmental variables change for each and every one of our distributed team members and with it so too does complexity. having solutions that give us deep introspection and the ability to report on and measure risks at the edge are huge.
The goal is to deliver an exceptional user experience and support services to these team members while at the same time developing systems, processes, and technology that allows us to mitigate and minimize security risks.
The users Identity
Azure Active Directory Identity Secure Score does a wonderful job collecting information around the security posture of our identities. With a host of prescriptive recommendations like limiting administrative rights or requiring multifactor authentication you can see where your organization compares to other organizations of like size or even in like industry.
With identity being the root to access many applications, networks, systems, and cloud resources it is imperative we have full visibility in the risk our identity policies / or lack thereof are placing on our organization.
The users Devices
When it comes to devices there are a few segments of the workspace that Microsoft recommends we focus on. Together these recommendations and observations of your endpoint deployment devices go into forming the secure score. each device is measured and scored on the following factors
-
Application
-
Operating system
-
Network
-
Accounts
-
Security controls
Remotely captures both this information per Microsoft Azure API’s as well as with our PowerShell Agent that is deployed to selected endpoints for deeper risk analysis and productivity visibility.
The users Applications. With local admin rights users tend to install applications extensions and toolbars they believe will help them do their job more efficiently or that have presented themselves during their daily click stream. While many of these applications have known CVE vulnerabilities which can be the root cause of exploits, their mere presence presents a management burden for administrators.
The combination of managed applications unmanaged applications unmanaged and unmanaged devices in a complexity of locations compels us to simplify our corporate images which will help decrease exposure and risk to exploits. Unmanaged software and Internet downloads are a superhighway through our VPNs.
The users Data. Here we are concerned with the location of user data. Do we manage, does the user manage, or do we BOTH manage storage for this identity? The answer is critical as policies need to be put in place that control the ingress and egress of data. Are the hard drives we provision encrypted? is sensitive user data or configuration information backed up?
Every one of these considerations can have both productivity and security implications. We recognize there are also cost impacts for any technology decision, and we believe there are also cost avoidance measures that can be taken around user data.
Connected storage is both incredibly useful and incredibly dangerous to end enterprise. not only is this storage unmanaged, it's unencrypted and often portable. having a full audit log of activity across our network will ensure that not only does our Microsoft secure score around data improve our field practices do as well.
Supporting content
How RMF Solutions Built on Microsoft Azure Are A Value Add

Microsoft is the gold standard within the modern enterprise as it relates to the applications and services used. The time, energy and effort together with investments in people and process most organizations have made around Microsoft and specifically now their cloud solution Azure is quite remarkable. For this reason we felt it critical to build our platform on Azure to augment and extend these investments as well as providing a globally available fabric to secure and support the largest agencies organizations and enterprises around the world.
The workflows and routines and integrations and API access for any solution on Azure is almost boundless, and allows organizations to imagine solutions versus being constrained in boxes. Extend this to our newly created RMF solution and what you see is the liberation of data typically held in silos.
Graph API from Azure gives us the ability to interact with data streams previously unavailable, or land locked behind a single console. Microsoft Intune, Microsoft Defender for Endpoints, Microsoft Secure Scores, Exposure Scores, Endpoint Compliance, Encryption, Licensing, Location, and Use can all now be unified in one data set allowing teams and task one single source of truth for their Risk Data.
With the countless Windows laptops, desktops, and servers deployed around the world in Remote Offices, Branch Offices, & Home Offices simplicity and minimalization in our attack surfaces is key.
Built as an Azure Enterprise Application RemotelyRMM inherits the security principles of Azure. From secure access, to load balancing, availability zones, and data compliance we can all leverage the massive investments Microsoft has made securing the Cloud.
The Truth About Azure & Risk Management Frameworks for Enterprise End Users
You may be wondering why other clouds were not considered for our initial release of RemotelyRMM. In fact -they were - and are! Remotely is built in Docker Containers and as such can run on nearly any infrastructure.
As you might imagine there is a tremendous interest on the part of Managed Services Providers to offer RemotelyRMM as a managed service. Distributed User Risk Reduction as a service is right around the corner. To enable the agility needed in these scenarios we are working now on deployment options on prem, or in other clouds as situations requires.
Enterprises, Agencies, and Organizations throughout the world have continually invested in the products, people, and processes that Microsoft solidified as the standard. There are significant challenges associated with managing massive end-user populations that always become more prominent when change is present. While we are highly confident the tech stack we use to power RemotelyRMM will be hugely beneficial to you - let us know when flexibility is needed.
Teams and companies that have leveraged Microsoft Azure the various services such as Teams, PowerBI, SharePoint, Microsoft Defender, AzureAD, and Intune, together with Office 365 have experienced a great deal of increased productivity. The larger our center of gravity in and around "standards" the more we can focus on our core businesses and less on one off configurations or support which can be costly.
We are very proud of our ability to unify all of the metrics, measurements, and data across these Microsoft Solutions and Offerings into one Unified Console. This new data lake is the source of truth for your Risk Management Framework implementation(s).
Anything you can measure - you can manage.
For large companies, basic needs must be met including safety, security, seamless adoption by your team, simplified billing, and cost exposure are critical.
So, what are the most prominent elements available on Azure?
- Azure AD—Cloud-native MS Directory Services that are Secure.
- Instant Scale—Azure is available throughout the world.
- MS Graph API—Enjoy easy integration with all other existing MS services
- Ease of Deployment—Simply right-clicks to deploy to up to 100,000 users.
- Easier Billing Solutions
- Scale Economy –Zero upfront capital costs for hardware—simply pay as you go.
- Roadmap Visibility thanks to their closeness to the future of Microsoft & Windows
- Enterprise Adoption
- Accelerated growth and closure of MS business
- Improved Admin Experience with Azure Services
- Easier Azure Active Directory Integration, Context within Organization & Deeper User
Introspection
- Office 365 Integration
- Security
- Increased Performance
- Daily Morning Health Check in Device Configuration
- Office 365 OneDrive whole disk backup
- Microsoft Graph API (Viva, Glint)
Supporting content
Step by Step into your RMF Implementation
Where to Begin: Identifying Endpoint & Remote User Risks
Step One: The Assessment
The first actionable step we take in our Enterprise Risk Management Framework is to identify and collect as much information about the end to end to end systems with an Assessment. Here at Remotely we call ours a TotalView™ Assessment. With such a rich tapestry of technology being orchestrated to deliver our remote user's digital day we should collect as much information as possible. Historically we would have needed to use several different systems to get information on our endpoints, our networks our applications, our licensing, our compliance identities et cetera. this alone adds complexity, cost and risk of human error into our analysis. We built Remotely to unify the previously disconnected consoles we all need information from into one cloud native source of truth.
The TotalView™ process begins by attaching natively to your Azure tenant with a set of pre-determined permissions as a service principal. Via Microsoft GraphAPI we collect information from Azure Active Directory Microsoft endpoint manager intune as well as Microsoft defender for endpoints among other data feeds. This paints an enterprise Dashboard as shown above to serve as an aspiration scorecard of our journey to manage risk across our remote users.
With a full view of each group in our organization the users within those groups the devices those users are using as well as the applications and storage their content is distributed across, we can prioritize and target groups for next steps In this case we want to deploy our PowerShell agent which can retrieve any kernel level metric needed. For our generation 1 offering we have pre-configured hundreds of bids of information that begin to show us the gaps, vulnerabilities and risks of each end point. We also know there is a keen interest in system performance and the ability to collect processor memory storage and network performance and security is also something we collect.
In a following section you will find a sample deliverable of what a TotalView™ Assessment and Findings Report might look like for your organization. Often much like Google Maps if we want turn by turn directions to our future state, we must know our current state. Additionally, our ability to create baselines of both system performance, digital user experience and security risk posture will help us improve and measure those improvements over time.
In a matter of minutes Remotely returns a host of information in which our endpoint and remote user risks can be exposed. oftentimes it is simply the utilization or policy enforcement of an investment we have already made that is the solution while other times it is the introduction of new technologies. Visibility drives improvement at the individual and group level.
Next Step: Analyzing Endpoint & Remote User Risks
The ability to look out across our entire enterprise and the groups that form the functional areas of our business and rapidly identify areas of concern, question or improvement is extremely powerful. Visualization can often help drive prioritization. The ability to observe how we are adhering to or deviating from our own security and compliance policies is the first analysis we should focus on.
Remotely synchronizes with Azure Active Directory and therefore inherits your fully populated directory of groups users etc. we use this information to begin analyzing the findings from the assessment phase of your projects. We often hear that based on findings at the group level projects will begin at a deeper level often considering additional stakeholders in security application or licensing teams.
Groups that show low secure score or high exposure score together with elements of licensing or system performance can now be analyzed in one unified console across teams. With our mission being heightened security and managed risk we can enlist all our teams into the defense of our company. Having one unified console with the information we used to cut and paste from different systems helps this effort tremendously.
The ability to detect anomalies in terms of adherence to policy or system performance or environmental variables can also be extremely useful as often it is good users who drift into a bad state that poses significant risk.
Other vectors can be selected as well such as applications which are observed across the environment or specific device types of ages manufacturers and more. The locations of users may also be concerning to management, or the change of location of a user or device may trigger the change of a policy, regulation, or rule. The dimensions of complex remote work added to our risk management frameworks are incredible and yet manageable with proper software.
Actionable Step: Prioritizing Endpoint & Remote User Risks
There are many corporate drivers for risk management frameworks chief among them tend to be financial. The cost of a security incident or breach is now in the millions of dollars and can impose even larger costs in loss of reputation or business momentum. one quantifiable metric in this domain is cyber insurance premiums. We have heard from several organizations that they are selecting to prioritize projects based on the largest impact to the bottom line in this case the mitigation of insurance premiums or cost of potential breaches. While one is more difficult to calculate, the first is quoted to us yearly along with requirements of our business to document steps we have taken.
As it relates to our new work from anywhere populations, Remotely's ability to collect the risk information needed to validate our enterprise endpoint RMF's have an impact on lowering risk will assist in pushing back against these financial headwinds. The scope, scale, and severity of observations, or the impact of past incidents can be used to assist in prioritizing remediation projects. Have cyber incidents or risk in the past been user specific, time specific, or location specific? Pattern anomalies are a powerful way to isolate and prioritize efforts.
In other organizations strategic initiatives or competitive goals are what will drive the priority of projects and solutions. Budgets follow priorities and while there will be a large amount of conversation in this document about end user productivity, we are also concerned about the productivity of our staff members as well as the productivity of our budgets. This new normal has us seeking larger returns on investment from the technological decisions we make. Remotely proudly unifies what were previously dozens of screens and solutions that together cost money in time, energy, and overhead usage.
Team Enablement: Addressing & Correcting Remote Risks
When it comes to ransomware, increased fines and fees from a regulatory perspective, a loss of productivity, the cost of multiple consoles, impact of breaches – the most expensive thing is to do nothing. In any modern risk management framework, we need to conclude that doing something logical and with deliberate process can provide a successful outcome. we need to define what these outcomes are for our individual organizations however the process for addressing and correcting is often similar.
There is also a time component to our risk management frameworks. Are we looking to analyze something that has occurred in the past to prevent it from happening again? is there a clear and present threat to our organization that compels us to fortify our systems and process now in the present? Perhaps we are simply looking to add a new layer of cyber resilience moving forward to ensure that we do have the ability to push back against cyber insurance premiums ransomware and regulatory costs.
Validation Steps: Monitoring Remote & Distributed Users for Risk Mitigation
As we and our teams engage in tasks aimed at avoiding, overcoming, or designing around risk factors we must be able to ensure the business that we have created durable solutions. We use the term durable on purpose as we know new unforeseen risks will emerge and present themselves, so we must endeavor at all times to create durable and resilient deployment of technology to our end users - AND - have the frameworks in place to know when we drift from our preferred, or required risk posture. Real time data streams from the cloud - coupled with rich and robust information from our edge devices is widely valuable.
Additionally, as we do design, test, and deploy new solutions, equipment, and applications for our remote users it is now possible to have nearly instant feedback on the progression towards, or regression away from a desired secure state.
We would all probably agree that there tend to be, or can be, too many alerts in life and in our daily jobs and the ability to separate the signal from the noise is paramount.
Wrapping it up: Conclusion Steps
The ability to get clear and incontrovertible data on the risk your organization faces by and through the provisioning of technology to distributed teams is a powerful way to push back against the rising costs of enterprise risk.
Furthermore, with not just end users distributed, but also our tech teams - one unified console with each domains actionable data included opens up the collaboration between silos we have long sought.
Lastly, with the time, energy, and costs we have invested in and across our instrumentality it is always welcome to have the option to consolidate and unify screens and views.
Benefits You Can Expect from RMM Software

There are and always have been legacy ways to fix unreliable computer systems even those that are separated from the primary campus at a distance. What truly is important these days is finding a platform and solution that integrates the investments and standards you have made for example around Microsoft and Azure with the needs of your remote users. With the proper due diligence into the needs of your organization it's highly likely RMM software might offer your IT department a unique way to transform their operations, making them more efficient, effective, and even profitable. Here are a few other benefits of using RMM software.
IT Management In a Single Control Panel
Integrations with endpoint backup, security, ITSM, Help Desk, PSA, and even other software solutions make it easy for RMM dashboards to serve as your central focal point. It also reduces the number of screen techs and admins that go back and forth to solve problems.
With the prolific adoption and consumption of cloud based solutions like zoom ServiceNow slack Microsoft Teams Microsoft Office and Microsoft OneDrive we believe a single control panel makes a tremendous amount of sense for sysadmins managing users at a distance. Additionally in the mission to secure and support those end users security antivirus malware and configuration control must be at the admin's fingertips as well
Total Visibility
As we often say you cannot manage what you cannot measure however the good news is with telemetry data and sensors everywhere there never has been more information to process. For this reason taking data streams from both end user location configuration machine type and usage patterns together with consumption of cloud based resources like Office 365 begin to paint a complete picture of the digital day for the end user. It is by and through this level of visibility that we can begin to make smarter decisions. I'm not only the technology we provisioned to and users but also how we secure and support them.
While monitoring and alerts are key to visibility taking actionable measures based on triggers or observation is the new frontier
Scalable Automation
Streamlining and automating workflows allows techs to be more valuable to your team by reducing the number of time-consuming manual tasks required of them. This frees up their time to support users and endpoints!
Our theory has always been in a large organization if common problems are observed with common solutions satisfying them these should be logically incorporated into the workflows and tools available to admins moving. We are interested in always and at all times in allowing technology to be a differentiator, an enabler versus a burden on the company. we believe that not only will individual improvements manifest themselves in anna cross most organizations there will also be a great degree of learning and collaboration from multi tenant environments that will be explored in the coming years
Eliminates Reactive Support—Replacing it with Proactive Support
RMM software empowers service providers to get out of the death cycle of continually putting out fires and enables them to get ahead of potential issues. This, in turn, can help individuals avoid downtime and disruption while increasing their revenue, while pushing down costs.
All too often modern IT department's are in neverending fire drill mode the hope is that now by engaging in security and configuration assessments a large part of the triage work of the helpdesk is now automated away and when truly specific issues are observed can be immediately fixed no matter where the user or admin or machine or service is.
How RMM Benefits Large Enterprise Companies
Large companies need larger solutions. As mentioned in this document a few times - larger companies also tend to have too many solutions. This often creates the need for one off dashboards, or large multi user spreadsheets. Remotely believes this impedes productivity of your teams, and also creates a risk for your budget (cost), and risk of human error (fat fingering data).
Financial, productivity, and security risks were the targets for our legacy NOC and SOC's. Network Operating Centers (NOCs) and Security Operating Centers (SOCs) are the command center for data center and campus control. However, with soo many of our users scattered to the wind and not at our primary campus locations, it does beg the question - why is our security software still on prem? No longer do we solve things from a singular location and distribute them to end-users. We would prefer that we solve risk presentation once, and then distributed users "inherit" that security posture.
In speaking with many of the largest companies, agencies, and organizations across the world over the past year it became very clear that what we used to solve with our most brilliant minds in and across our primary headquarters now needs to be extended across unstable unreliable and often insecure networks. An entirely new category of cloud centric distributed device and user aware solutions where security is not an afterthought but a core provisioning principle are needed
RemotelyRMM is purpose built for the modern Enterprise to see, secure, and support their distributed teams by ensuring the presence of risk does not effect the productivity of our users, staff members, or budget.
Furthermore - as many larger organizations with seasoned Chief Information Security Offers (CISO) and Governance Risk Compliance offices can tell you - the implementation of risk management in any area of the business, while and investment, has durable returns.
How to determine your need for RMF Software

While there are vast differences between the products, services, systems, and processes modern organizations use to do business - there are also observable similarities. Most companies we work with have some degree of their user population that used to be on campus, and is now not there as consistently. Others have massive user counts that are now working from home, branch offices, or "anywhere".
The operative way we recommend considering Risk Management Frameworks for your organization is by starting with a well defined answer to the question: What problem(s) are you interested in solving?
- Lower Exposure Risks
- Cyber Insurance
- Ransomware Costs
- GRC Adherence Costs
- Incident Response
- Workplace Modernization
While reliability and performance can vary greatly from one RMM to the next, the majority of legacy solutions sadly have the same core features. Very few, if any legacy RMM solutions have RMF considerations included.
One theme we share often is that with all we hope to accomplish by fixing remote users technology challenges - if they cannot PROVE they are not a risk to themselves or others - we might prefer to turn them OFF, or keep them off of our networks.
We purpose built RemotelyRMM to unify the worlds of RMM and RMF. However, we also spent a ton of time on product stability, customer support, and ease of use, cost, and security response time and value, among others. This is a solution for you!
Simplicity of Setup
Without getting too technical here - RemotelyRMM connects directly to your Azure Tenant as a Service Principle / Enterprise Application. As such, there are a number of permissions from and across Azure, AzureAD, GraphAPI, Microsoft Defender, Microsoft Intune, and others required for API access.
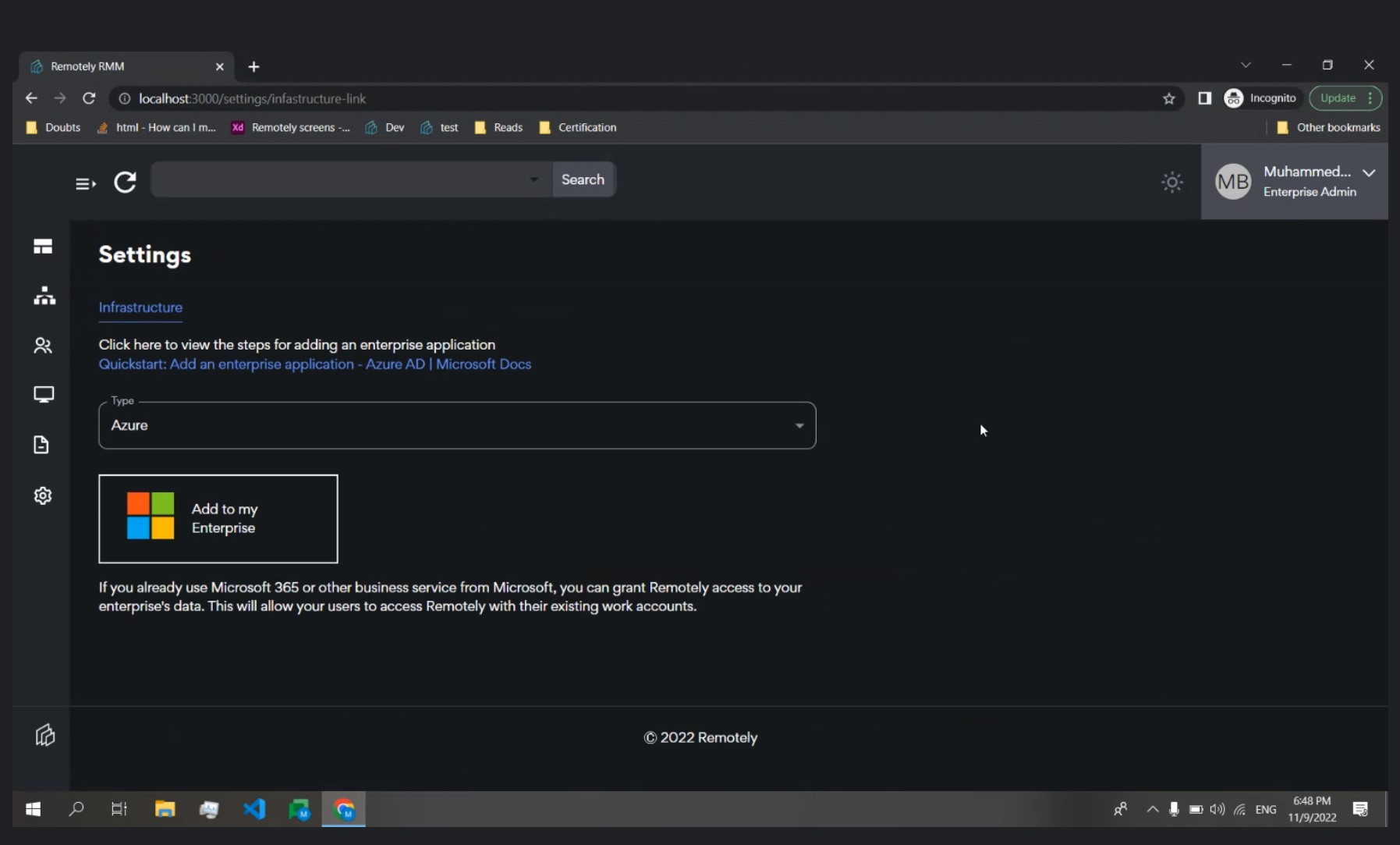
We have streamlined ALL of this for you - so Simplicity of Setup is four clicks from start to finish.
- Request Access to RemotelyRMM
- Confirm your email
- Connect to your Azure Tenant
- Synchronize with AzureAD
Your Enterprise Dashboard, entire AD Group Structure, users, devices, and applications will all populate automagically in the console. You can browse compliance, security, updates, configurations, and more with our intuitive console.
** RemotelyRMM once configured brings in data on ALL OF YOUR USERS, in all groups **
From there you have access to deploy our native shell agent (PowerShell) to any or all users across your organization. Use the observed groups above to prioritize and plan your project steps based on risks you see or wish to address.

Once registered, our agent relays information on system state, location, applications, cpu, memory, network, storage, compliance, firewall rules, local and group policies applied, Windows Logging, and so much more!
Reliability & Stability & Availability
Our ability as an organization to deliver successful outcomes is often limited in two dimensions. Dimension 1. are the tools and solutions we choose. These directly impact our ability to find root cause, automate fixes, scale actions, & avoid patterns. Dimension 2. is time. Time is the most valuable asset any of us have, and it is far from a commodity. Too often our teams and tasks spend TIME we would prefer not to. Our need to standardize data, measurements, and metrics across a myriad of tools takes away from this (and costs more).
For that reason we selected Azure as the primary host for RemotelyRMM at this time. With a majority of our organizations and users relying heavily on MS solutions it is only logical to nest among this rich data repository and make full advantage of the data streams to lower enterprise risk.
Remotely is Software as a Service, SaaS, with no need to acquire, configure, secure, and maintain any additional infrastructure. Availability, load balancing, speed, and security are all inherited from Azure and go to great lengths to ensure the reliability and stability of Remotely.
From an availability standpoint the global footprint of Azure allow organization of any size, in any location, under any operating circumstances to tap into the power of the cloud.
A Risk Management Framework, if implemented thoroughly and properly, should always have a watchful eye on your user count to ensure the minimization of risk
Customer Support
In any new domain, specifically as it relates to Risk Management Frameworks, having phenomenal support as you become familiar with your solution set is of huge value. Having great documentation is also incredibly useful. We went the extra mile and have drafted Whitepapers, Solutions Briefs, Calculators, Consultants Delivery Guides, among other assets. Together we hope these form a "Methodology" for you to use in exploring, tracing, and erasing the risks you face.
If you are in the primary business of supporting your end users and reducing risks, make sure your vendors takes its responsibility to be available for you 24/7 365 very seriously. The availability, access and uptime of the platform should be taken into account as well as feedback in forums, wikis, social media, product comparison sites like G2 or Capterra etc.
There are two things you should never be too frugal on, one is toilet paper and the second is customer support :) In all seriousness, we cannot wait to support you!
Ongoing Administrative Needs
Managing your software experience across teams is just as important as the licensing fee. The time, expertise, and effort it takes to manage it are equally important. instead of requiring organizations to make large upfront capital costs we decided the first administrative need is to pay as you go. We offer flexible pricing, subscription, and use options - just ask. We want your entire administrative experience working with Remotely Inc. to be your favorite.
Upfront investments in time personnel and training work against the primary mission of keeping admins budgets and users productive. We are SaaS. You can subscribe for 1,348 users, or your entire global enterprise.
There are a few other ways to extend and expand your administrative experience. Chief among them are to apply to be a part of either our Early Adopters Program or our Remotely Technical Advisory Board - both pending.
A Customer Sourced Road Map
You tell us what to build, when to build it, how it should work, and how much to charge. You are never an interruption of our work here, your are the REASON for it (thanks LL Bean) for a wonderful quote. We have some amazing definitions and visions based on your initial feedback, and as you can see we love it when your ideas help the community.
Concluding Thoughts
The problem statement we all faced over the past few years is quite daunting. Take 50% of your 1 billion corporate technology users and cut the cord - quite literally. Now offer the same level of security and support, at the same cost, as when there were nicely nested in their cubicles. Good luck.
Taking a step back and beginning to think about how to re-architect the new normal and remote distributed team member can actually be an opportunity. In fact - we see the introduction of a Risk Management Framework (RMF) in your organization as a foundation of data off of which progressively less risky ideas and solutions are born. The chaos quickly quiet when you realize you can now assess secure and support your end users no matter how large the fleet is from one central location in the cloud nested among the core solutions and standards your company already has made
Create new opportunities and innovation and enjoy better performance and outcomes for your end users your staff and your budgets worldwide.
About Remotely
Remotely is a modern enterprise grade Risk Management Framework for Enterprise End Users platform built in Azure.
RemotelyRMM provides an all-in-one tool set built to enable the offices of the CISO, CISSP, System Administrator, End User Computing & Virtualization Architects, Governance Risk and Compliance teams, along with a host of Security Practitioners to unify in the fight against enterprise risk.
By simplifying and automating the day-to-day work of IT professionals, they can spend more time focused on complex, value-added services, end-user relationships, and strategic projects.
Take a deeper dive.
Request a live, personalized demo of Remotely and see the industry's only Azure native RMF +RMM solution in action.
Contributors

Tyler Rohrer
Founder & CEO, Remotely
Sources:
From Our Blog
Stay up to date with what is new in our industry, learn more about the upcoming products and events.

The Worst and Best Day of Your Company's Life

The Most Dangerous Threat Is The One You Can't See

.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)
