TECHNOLOGY OVERVIEW
Helping remote enterprise teams to monitor, manage, and protect distributed users.
Key Components
Remote Monitoring and Management software provides visibility and tools tailored for management of remote end points. Remotely is designed for the way modern enterprise organizations operate.
Remote Monitoring & Management (RMM)
- Visibility
- Reporting
- Interaction
- Support
Security
Enables visibility to security posture and potential vulnerabilities of remote users
- Visibility
- Reporting
- Policy Management
- Quarantining
Azure Integration
Integration with Azure stack including visibility to key O365 metrics
- Visibility
- Reporting
- Utilization
- Savings
Remote Monitoring & Management Tools
Visibility and tools tailored for management of remote end points.
Support
Interaction with the end user experiencing the problem is often the difference between good service and great service.
Interaction & Support
Dashboard is the central hub for the Remotely solution. The remote administration toolset will assist admins in providing support to end users when experiencing situations
Targeted tools for Administrators
Remote PowerShell
Ability to securely run PowerShell commands and scripts on remote endpoints for users
Integration with existing enterprise tools
Remotely RMM with focus on helping enterprises leverage their existing technology investments in new ways to meet the changing needs of security and support
Targeted integration platforms
- Microsoft Teams
- Zoom
- ServiceNow
Visibility & Reporting
The Remotely RMM Dashboard is the central hub for the Remotely solution. The data collected from our endpoint agent is displayed for use by the administrators within an organization, each component is broken down into various granularity levels from overall enterprise to individual device.
Measurements collected include
CPU performance
- Utilization
- Queue length
- Interrupt time
Memory performance
- Utilization
- Faults
- Page file utilization
Disk performance
- Read/Write performance
- Queue length
- Free space
Network performance
- Transmit rate
- Receive rate
- Packet errors
Network configuration details
- Connection Type
- Signal strength
- Connection Security
Environmental variables
- Connected device
- Enabled protocols
- Policies
RMM – Architecture Overview
Roles Based Access
Roles based access controls are enabled within the application to limit visibility of data and refine focus to relevant information for user roles.
Application Admin
Application Admins are Remotely employees who have access to view, update, and configure account settings only. No endpoint data or configuration is accessible.
Enterprise Admin
Enterprise admins are client administrators that have access at the overall company level, all data is visible to administrators at this level.
Organization Admin
Organization admins are client administrators that have access to specific organizations within a company, only data within the defined org is visible to administrators at this level.
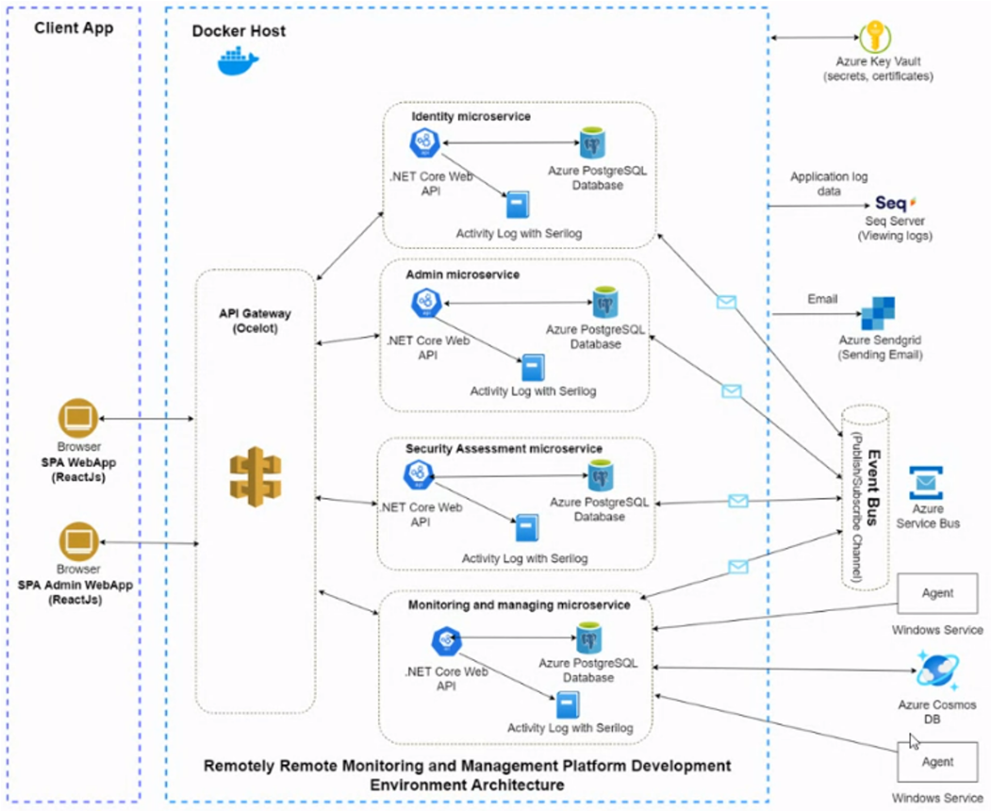
Microservices
The application architecture is designed with security as a core tenant, by utilizing segmented microservices we enable faster iteration releases, reduce potential attack impact and reduce our attack surface by only exposing API connectors.
Identity Microservice
Application authentication will be conducted through the identity microservice, entirely segmented from any application information
Admin Microservice
The admin microservice will host key functions for application administration, entirely segmented for any collected information
Security Assessment Microservice
Data collected from Azure tenant for security configuration is stored and processed within this microservice then displayed via API to admins
Monitoring & Management Microservice
Client data collected from endpoints is stored and processed within this microservice then displayed via API to admins
Security
A security posture focused solution to supporting edge devices
Visibility
The Remotely Secure Dashboard provides real time visibility to the security posture of an end users device and environment.
Reporting
The security reporting dashboard gives insight into past security postures and changes over time, at various levels in a single view.
Policy Management
Understanding the security policies that should be applied to a remote device is critical to understanding the user experience.
Quarantining
(Coming soon) Adaptive policy management based on environmental and observed end point risk factors.
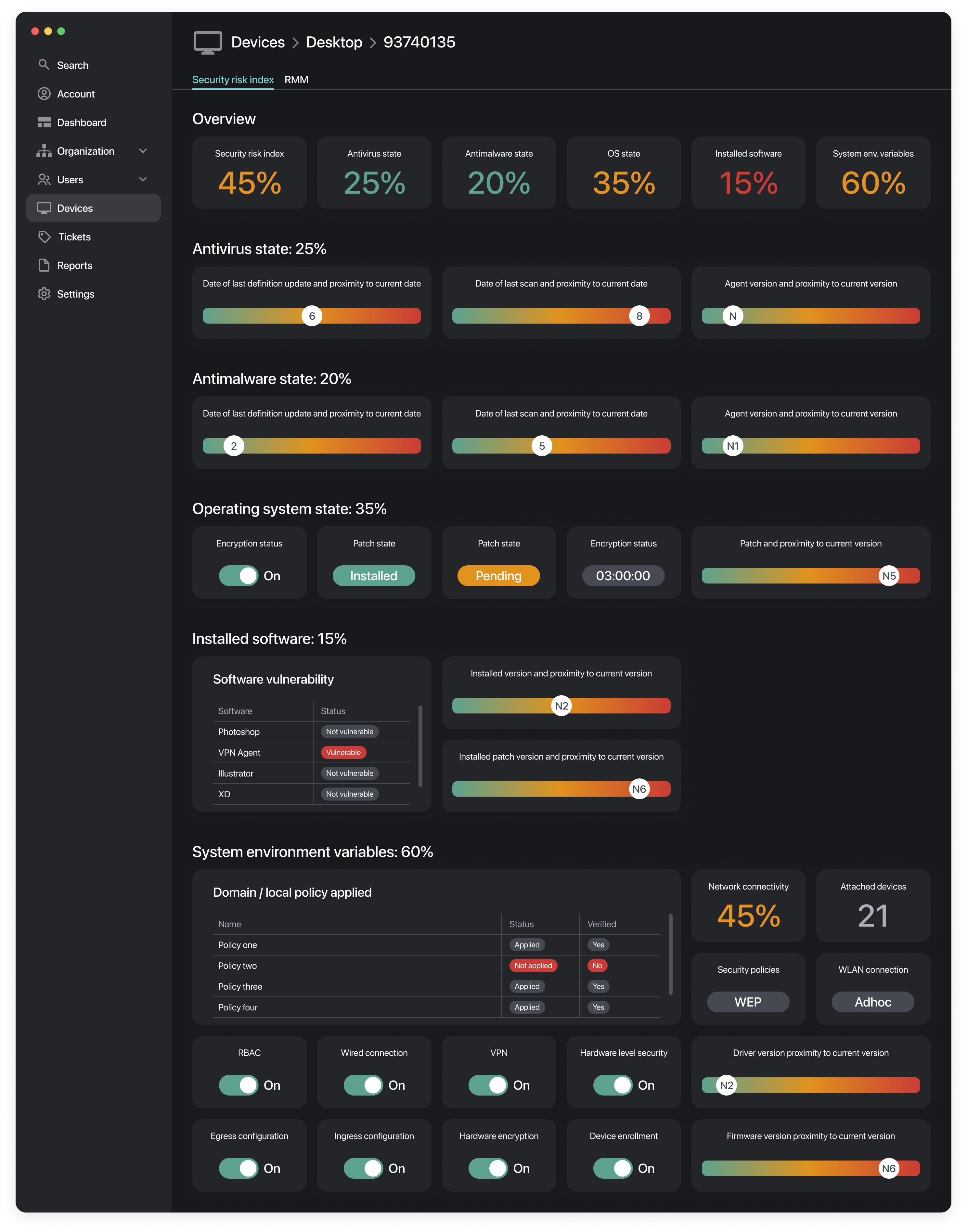
Adaptive Policy Management
Utilizing the power of Azure cloud, Microsoft Endpoint Manager, and the information collected by Remotely adaptive security policies can be applied to edge devices based upon their potential risk.
Know Your Edge
Being able to make and automate informed policy actions based upon the operating environment for an edge device will be a key feature of Remotely enabled adaptive risk management practices.
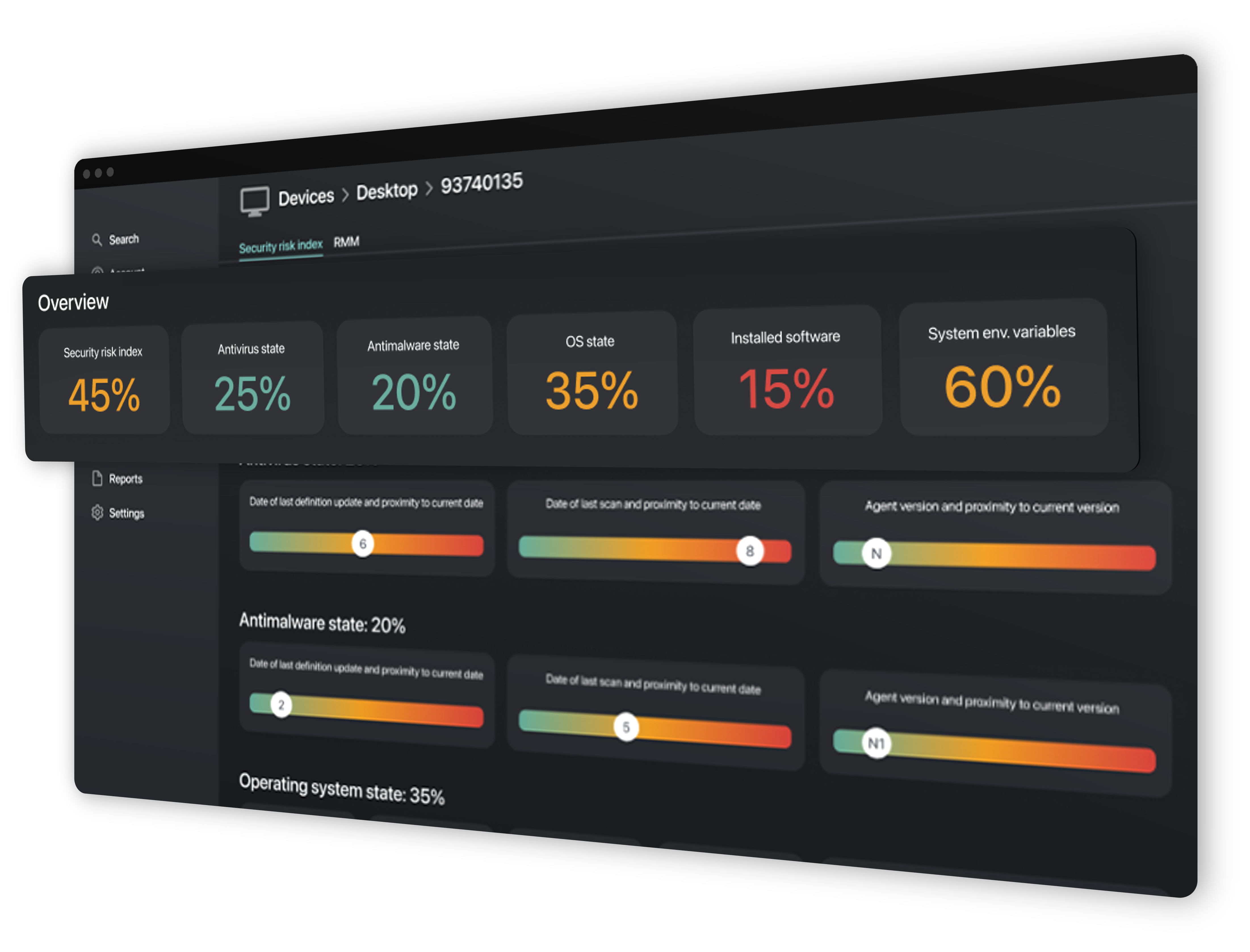
Measurements Collected
- Anti Virus State
- Anti Malware State
- Operating System State
- Installed Software
- Network Connectivity
- Environmental Variables
- Attached Devices
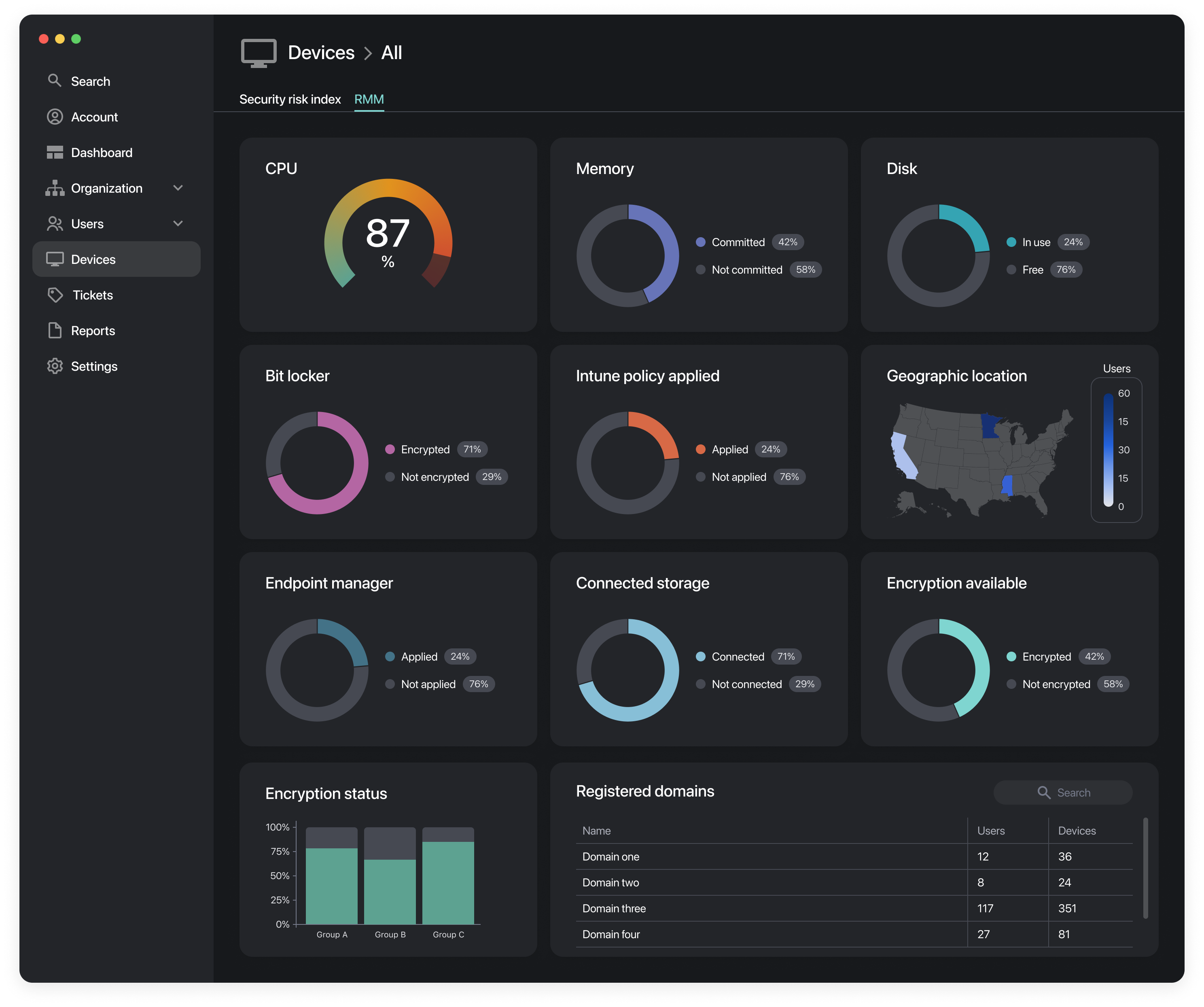
Security Threat Score
A security posture focused solution to supporting edge devices.
Utilizing information collected from the Remotely endpoint agent a calculated risk score is determined across the organization, from the individual device to the entire enterprise.
Security Threat Score
Understanding the environment and health of remote systems can be a challenge and keeping unsafe systems healthy and online exposes enterprises to risks that many do not know exist.
Measurements Collected
-
- Anti Virus State
- Anti Malware State
- Operating System State
- Installed Software
- Network Connectivity
- Environmental Variables
- Attached Devices
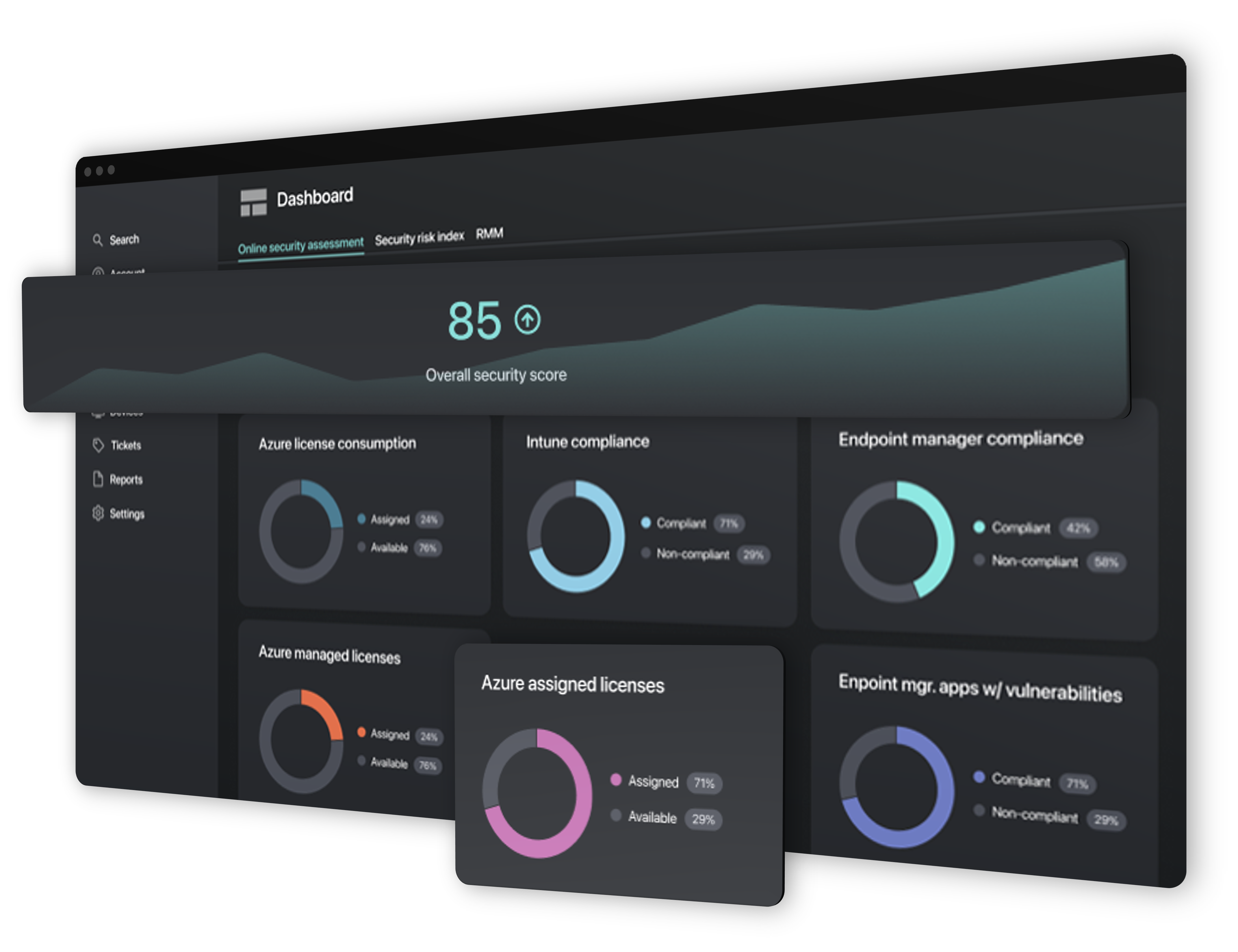
Online Security Assessment
A security posture focused solution to supporting edge devices.
Working to help bridge the divide between security and support Remotely gives unique insight into the risk posture of devices connecting to enterprise assets and networks allowing administrators to take informed actions.
Online Security Assessment
Gathers information from Azure into one easy to consume dashboard for your current security model with a focus on endpoint configuration and risk.
Data driven planning
Using the data collected by Remotely Online Security Assessment organizations can determine the best path of investment to reduce their risk landscape within their Azure configuration and deployment.
Configurations assessed
-
- Microsoft Endpoint Manager Deployment
- Azure Licensing
- Microsoft Windows Update Rings
- Registered Enterprise Applications & Reported Vulnerabilities
Azure Integration
Remotely is the first Azure native RMM and edge security solution. Enabling increased adoption and better leverage of existing technology platforms & investments reducing the learning curve associated with new software.
Visibility
Remotely taps into the vast data lake underneath Azure to provide a unique view of the user and how to optimize their environment.
Reporting
The Azure reporting dashboard provides a single source for all user information including Azure interactions and system performance.
Utilization
Understanding how end users are leveraging technology is critical for organization to ensure they are empowering users in the right way.
Savings
Understanding how end users are leveraging technology can ensure that the right services are provided to the right users.
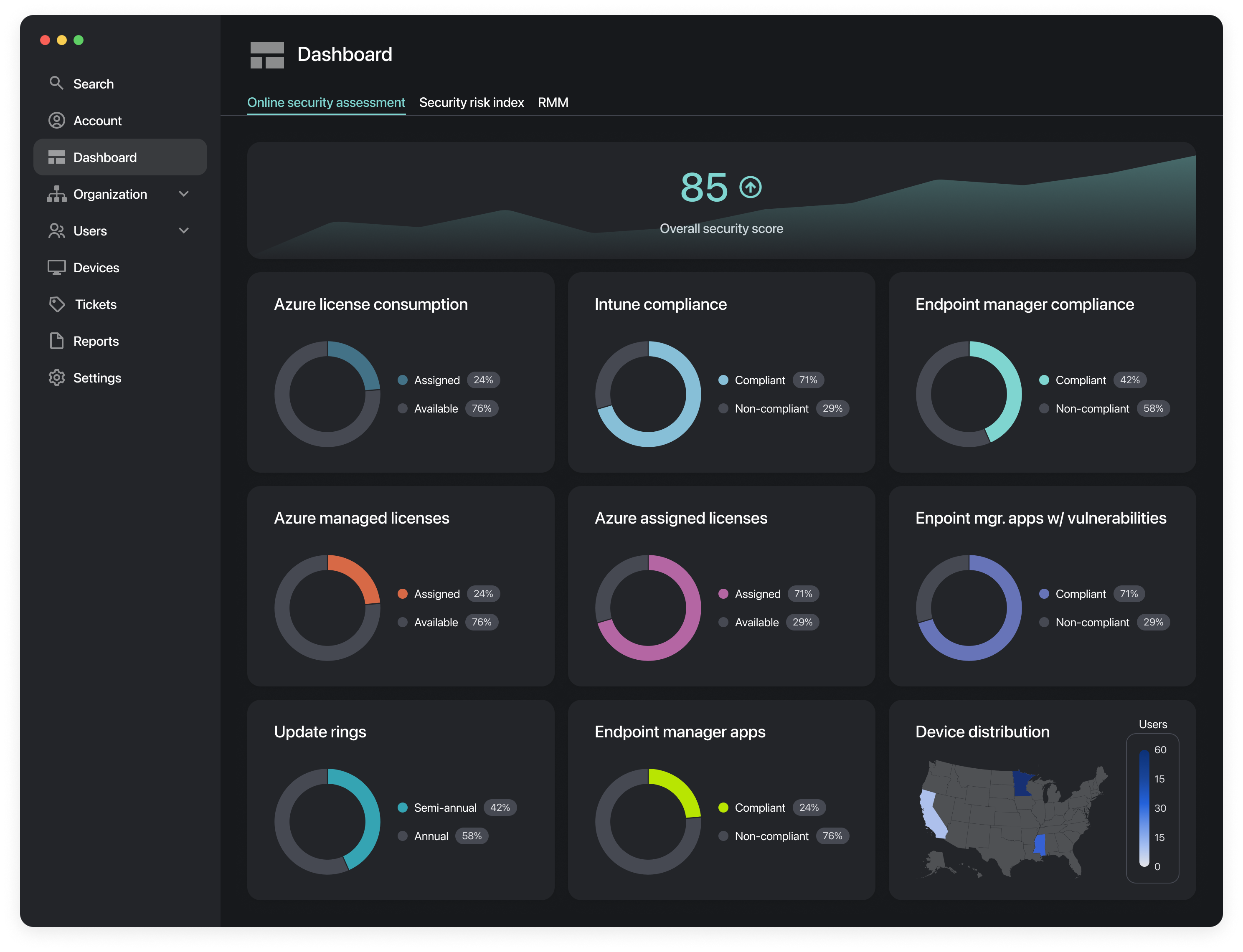
Integration with Azure stack including visibility to key O365 metrics
Geolocation services
Allows geolocation of managed assets and users to ensure that authentications and access are genuine and enable better visibility to the enterprise global distribution.
Enterprise Applications
Provides visibility through a single dashboard to all enterprise managed applications and any potential associated vulnerabilities.
Microsoft Licensing
Gain visibility to licensing within a Microsoft Azure tenant including Managed, Assigned, and consumed to ensure that applications are used or reallocated to reduce cost.
Azure Security
Building a modern application in the Microsoft Azure cloud enables leveraging of the industry Microsoft
industry leading application security framework
Azure Graph API
Utilization of Microsoft Graph API for data interaction significantly reduces the risk exposer by leveraging existing defined Azure security principal roles with the enterprise
Azure Cloud
Workloads within the Azure Cloud are deployed as members a micro-segment security framework providing port and protocol level isolation, traffic flow and monitoring
Concluding Thoughts
The need for enterprises to control their remote devices is accelerating.
Since even before the pandemic, enterprises with remote and hybrid workforces saw security risks increasing. The #1 most feared risk? Technology issues: cybercrime, IT failure, and data breaches.
The need for enterprises to control their remote devices is accelerating.
Since even before the pandemic, enterprises with remote and hybrid workforces saw security risks increasing. The #1 most feared risk? Technology issues: cybercrime, IT failure, and data breaches.
Enterprises IT teams are struggling to secure remote and hybrid networks.
Today, tech teams report being understaffed and ill-equipped to support and secure remote and hybrid workforces. Moreover, when tech problems arise for remote employees, it can genuinely affect the company’s bottom line.
And this is why Remotely set out to build a holistic platform for hybrid enterprise teams to monitor, manage, and protect their distributed users.
Contributors

Tyler Rohrer
Founder & CEO, Remotely

Eddie Riddle
Chief Technology Officer, Remotely
.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)
