Remote Work Risk Assessment
by Tyler Rohrer on November 27, 2022
Assess or Guess?
We are at a unique crossroad in end users computing in that never before have we seen such large numbers of users suddenly change primary and daily work locations. This has given way, as we know, to changes in daily workflow, device choice, application use, and security adherence, among a host of new challenges.
An assessment gives you a granular look at your current state. Armed with this information you can design to, execute to, or avoid - a future state depending on your tactical and strategic plans or constraints of your organization or team. Speaking of teams - having everyone from GRC to Security to DevOps to End User Computing, Help Desk, System and Network Administrator using ONE DATA SET is golden. We built RemotelyRMM for risk management across teams - so everyone is in on the plan. As they say - if you don't have a plan you are more than likely going to end up as part of someone else's plan. Bad actors know this. If we turn on the lights in a dark room - we see the good, the bad, and the ugly. If all of our teams see the same things in the same way we gain massive efficiency.
An assessment can and should provide multi-dimensional data that has several use cases that allow us to move past tactical survival and finger crossing, into meaningful action on behalf of your company. Now reality precedes the best planning we often need to, and can, use assessments for tactical, point in time use cases, or when time and budget permits, or situations dictate - longer term projects. The bottom-line we always arrive at is good data, wide data, aid in good decisions.
Project types benefiting from remote user assessments:
- Remote / Hybrid User Survey - where are we now?
- Cybercrime Insurance Premium & Risk Mitigation
- M & A activity
- Remote, branch, home office rationalization
- Incident Response, Threat & Risk Hunting
- Next Generation Workspace Plan, Design, Optimization
We have the unique ability with RemotelyRMM™ to collect compliance, policy, location, licensing and more from across the various Microsoft services our organizations use such as Office, Teams, SharePoint, Defender, Endpoint Manager/Intune and more. The real context of a day in the life of our users happens at the edge. So, we built an agent. A really really good agent in native shell (PowerShell) that can see and therefore know, anything, up to every few seconds when need be.
In the context of our definition of Assessment - information must be available from the edge all the way back and through to the cloud services your organizations owns, secures, and uses. This will unify our teams and tasks.
Now, the edge is more risky than being safely LAN attached at a primary campus location, and always has been. Users at a distance are both more difficult and expensive to manage, they also pose a larger volume of attack vectors. These days nefarious actors with mixed intent (including insiders) lurk everywhere. The term zero-trust seems appropriate as our legacy perimeter based security solutions, once breached, are of little use. The number one feedback we got in starting remotely was lack of visibility into remote team members.
SIEM and XDR based solutions tend to benefit us primarily right of BOOM, dealing with the forensics and management of incidents for future hardening - and even then we have focused on antivirus and malware - as we should - now its time to add risk, policy, and configuration information into the equation. Shifting left of Boom shifts our mindset to security policies and procedures, if followed, harden and prevent - or perhaps just discourage and thwart threats.
For the sake of initial simplicity (we can geek out later) we are going to focus on several primary categories of metrics relating to our distributed teams. We are huge proponents of conducing end to end assessments. An assessment is a picture in time that represents your "current state". Namely - what our team members have, what they use to create and consume content. We are interested in all facets of their digital day and this context gives us added dimensions versus simple system performance analytics (which are also needed and included :).
We are interested for a number of reasons. First we would love to be able to proactively observe, isolate, and address security risks. Secondly, we would be helped greatly if we could see where our users, systems, applications, policies, or processes are drifting from best practices, towards less secure states. Lastly, we want to insure we are ALL being productive - namely - users, our staff / team, and our budgets.
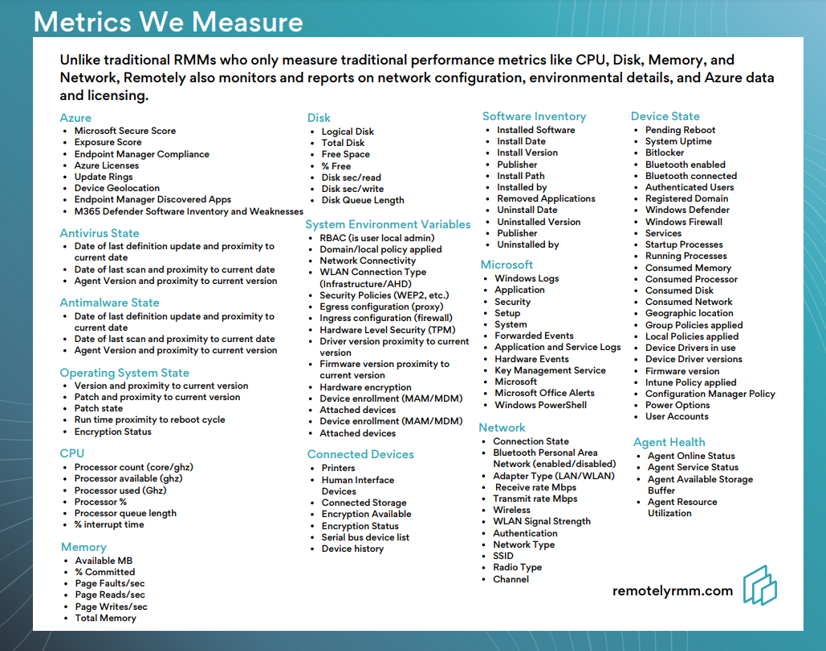
Our Remote Work Assessment desires to capture the following metric types.
- User Information
- Device Information - Windows™ system Logs, Printers, peripherals
- Application Inventory, Removal, Security State, and Information
- Settings - local, user, admin, group policies, and compliance
- Network Details
- Context & Behavior - how, when, where, and what do users do
User Information
We are charged with creating secure and reliable computer systems out of intrinsically unreliable parts. Today, with a smile, end users are the most unreliable, volatile, and abusive moving part we must contend with. 90% of all cyber incidents are caused by human error - and this typically involves not following the rules. Our Remotely TotalView Assessment collects all information for the user space - the systems, devices, accounts, domains, workgroups, licensing, location, apps, vulnerabilities, Windows Logs, Software Inventory and Usage and a whole lot more. We MUST know everything we can about the user.
Device Information
Users use devices to create and consume the content we ask them to in the course of their work. Corporate standards, budget needs, or personal preference tend to drive device selection in the enterprise. Today, and recently we have seen an increase in both BYOD (bring your own device) as well as supply chain constrained purchase patterns of lower end systems. The device is also extended to the devices, peripherals, smart phones, tablets, printers, and other technology we use in the course of our digital day.
Application Details
Applications are the tools our users use to consume and create content in the course of doing their daily tasks and jobs. They are also one of the single largest attack surfaces and risks we must contend with on a daily basis. Anti virus and Antimalware solutions are fantastic when properly configured and used. Our ability to inventory applications, isolate those that pose specific threats, or have known vulnerabilities or NIST CVE Vulnerabilities is hugely helpful in increasing our security postures and pushing back on risk.
Settings
We need to know if there is any DRIFT from our preferred, or required system settings. Are users overriding, ignoring, or changing settings that may expose the device, user account, or applications to additional security risks? We may deploy solutions like VPN's or managed firewalls - however - if users are not putting them to use we are at risk. With so many security dimensions to contend with the least we can do is manage how and when our end users break the rules and policies we set and then gently direct them back to our preferred state.
Network Details
One of the primary challenges with our remote and distributed team members is the myriad of networks they use. From home offices shared with family members, entertainment devices, and often tuned for throughput versus security to public coffee shops, transit locations or access points in between each poses a new security risk. In the course of using RemotelyRMM to conduct a TotalView assessment we want to know the names, security settings, performance,
Context & Behavior
This is perhaps one of the least studied and yet most interesting and realistic use cases for 500 million end users today and every day. Context relates to the how, when, where, and what a users does in the course of their digital day. This matters today because no longer is the location static. Static location was a variable we could plan for, secure, lock down, and monitor for drift. Users switch context all the time, and at a much more rapid pace with the work from anywhere generation and work style. For this reason the more we can understand and map these workflows the better prepared we are to use the totality of our assessment data to make decisions and avoid risk moving forward.
User behavior is also evolving out of a necessarily 9 to 5 workflow into one that is more on demand, agile, flexible. Assessments help us capture this new behavior to help us factor new evidence into our designs. Non linear, asynchronous work flows mean that every expects to work when THEY want to, without delay. Its a frontier mentality in end user computing - and VDI virtual desktop infrastructure, thin and secure edge devices, Desktop as a Service (DaaS) from all hyper-scalers are compelling for the right use cases.
Assessments always help us architect the stack - from edge to identity to data to apps to cloud services. It may be financial savings or security concerns or even competitive advantage that compel us to modernize our workplaces. What we cannot avoid is the headwind of risk cyber and analog security concerns present.
Armed with a full spectrum of assessment information we are empowered to address current risks, unpack past incidents, and architect solutions and stacks for your next generation workspaces. We can also dive into the dark arts of un-architecting bad decisions made over the past few years.
We have said in the past that we all are truly writing the pages of the book as we go. At no time before has a change in architecture met such security challenges and potential risk. The well architected workspace of tomorrow is being written today.
We are excited to be able to play a role in it, and invite you to come check out our solution with a Free 14 Trial.
Thanks for check in - next week we dive into SECURITY at the EDGE !!!
J Tyler T.Rex Rohrer
Add some fun, compelling content here
- Cyber Security (16)
- Security (15)
- Azure (10)
- Cyberattack (10)
- IT Operations Management (10)
- Remote Monitoring and Management (10)
- AIP (9)
- IT Strategy (9)
- Remote Work (9)
- Asset Management (7)
- IT Operations (6)
- Asset Inventory (5)
- Reliability (5)
- Remotely Interesting (5)
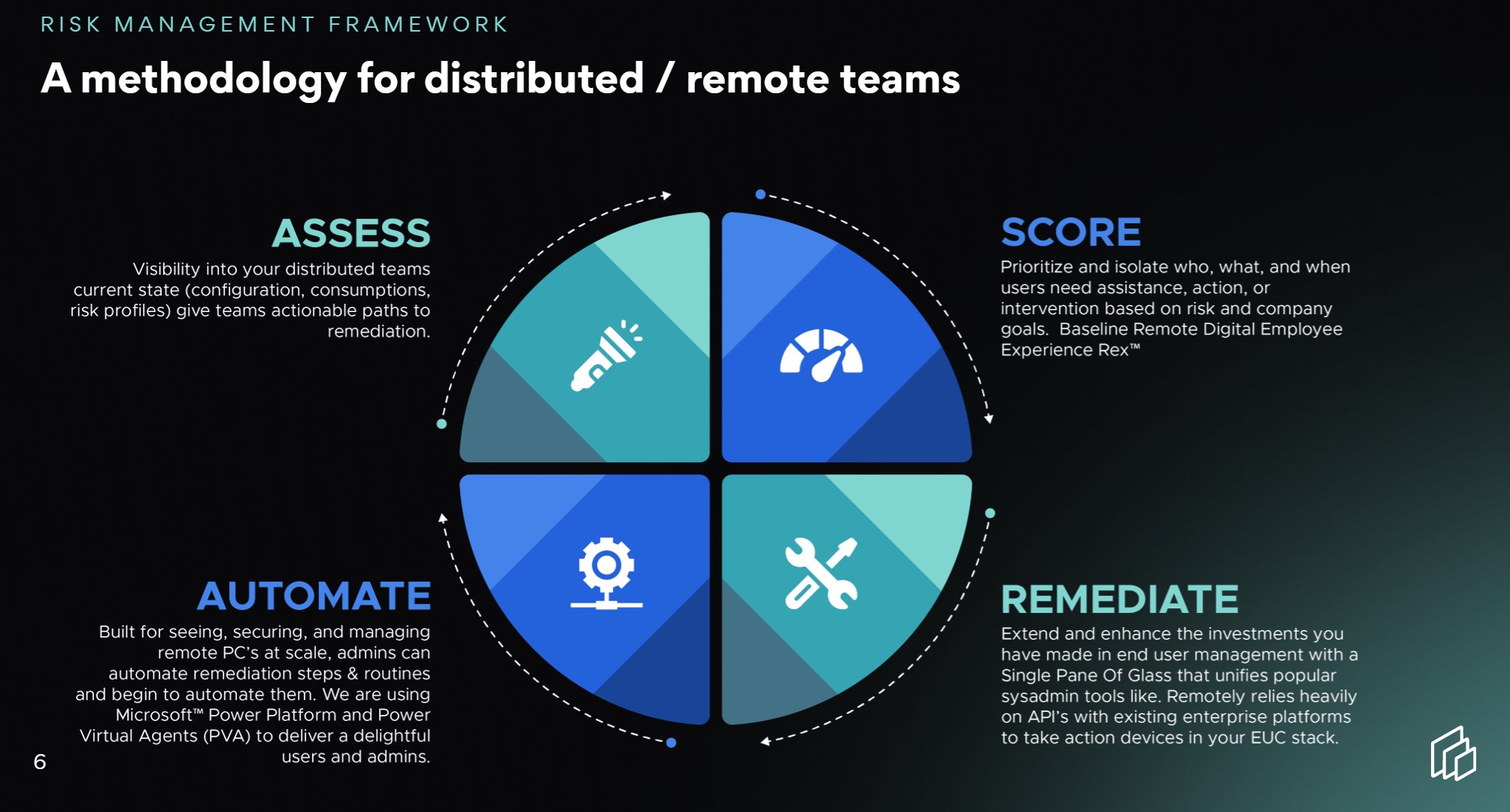
- Risk Management Framework (5)
- Azure Migration (4)
- Microsoft Secure Score (4)
- Office 365 (4)
- Security Risk Index (4)
- Customer Success (3)
- GRC (3)
- Risk Dashboard (3)
- Support (3)
- Powershell (2)
- First Steps (1)
- Migrate (1)
- System Requirements (1)
- Virtual Machine (1)
- Zero Trust (1)
- August 1, 2023 (1)
- July 1, 2023 (2)
- May 1, 2023 (1)
- March 1, 2023 (2)
- February 1, 2023 (1)
- January 1, 2023 (1)
- December 1, 2022 (2)
- November 1, 2022 (2)
- October 1, 2022 (1)
- September 1, 2022 (2)
- August 1, 2022 (1)
- July 1, 2022 (1)
- June 1, 2022 (2)
- May 1, 2022 (4)
- April 1, 2022 (3)
- March 1, 2022 (2)
- February 1, 2022 (2)
- January 1, 2022 (1)
- December 1, 2021 (4)
- November 1, 2021 (1)
- October 1, 2021 (1)
.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)


No Comments Yet
Let us know what you think