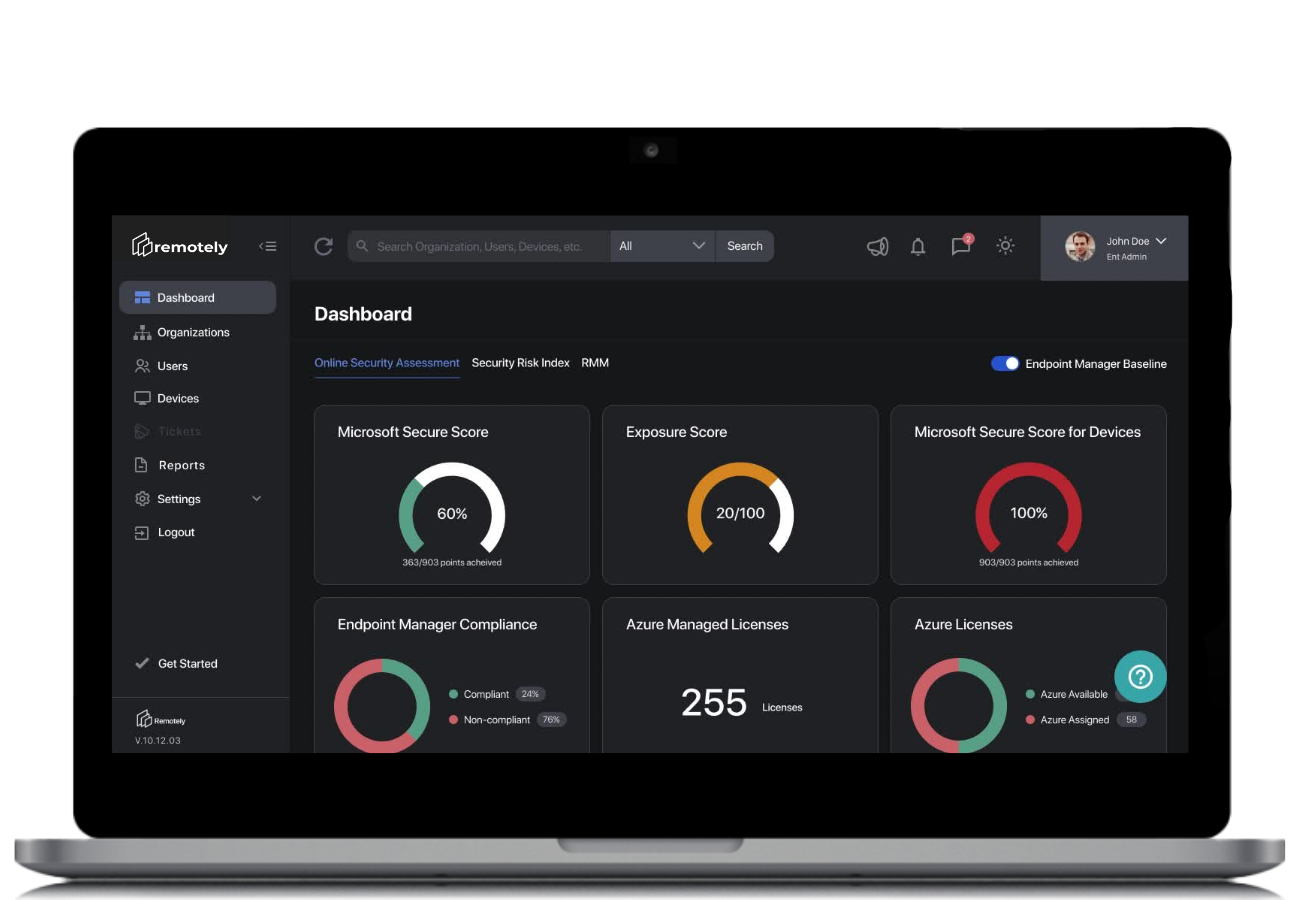
Easily Monitor What Matters
Metrics We Measure
In addition to tracking and reporting on standard measurements including CPU, memory, disk, and network performance, Remotely can report on.
- Date of last antivirus definition update and proximity to the current date
- Date of last scan and proximity to current date
- Agent Version and proximity to current version
- Disks Encrypted?
- Operating System Version and proximity to current version(s)
- Corporate Standard - or Rogue ?
- Patch and proximity to current version
- Patch state / Pending
- Run time proximity to reboot cycle
- Encryption Status
- Processor count (core/ghz)
- Processor available (ghz)
- Processor used (Ghz)
- Processor %
- Processor queue length
- % interrupt time
- Available MB
- % Committed
- Page Faults/sec
- Page Reads/sec
- Page Writes/sec
- Total Memory
- Printers
- Human Interface Devices
- Connected Storage
- Encryption Available
- Encryption Status
- Serial bus device list
- Device history
- Agent Online Status
- Agent Service Status
- Agent Available Storage Buffer
- Agent Resource Utilization
- Connection State
- Bluetooth Personal Area Network (enabled/disabled)
- Adapter Type (LAN/WLAN)
- Receive rate Mbps
- Transmit rate Mbps
- Wireless
- WLAN Signal Strength
- Authentication
- Network Type
- SSID
- Radio Type
- Channel
- Date of last antimalware definition update and proximity to the current date
- Date of last system scan and proximity to current date
- Agent Version and proximity to current version
- Installed software, versions, and verification against known risk database - NIST CVE
- Installed version and proximity to current versions
- Install Path for the application
- Uninstalled / Removed Software
- Logical Disk
- Total Disk
- Free Space
- % Free
- Disk sec/read
- Disk sec/write
- Disk Queue Length
- RBAC (is user local admin)
- Domain/local policy applied
- Network Connectivity
- WLAN Connection Type (Infrastructure/AHD)
- Security Policies (WEP2, etc.)
- Egress configuration (proxy)
- Ingress configuration (firewall)
- Hardware Level Security (TPM)
- Driver version proximity to current version
- Firmware version proximity to current version
- Hardware encryption
- Device enrollment (MAM/MDM)
- Attached devices
- Device enrollment (MAM/MDM)
- Attached devices
- Installed Software
- Install Date
- Install Version
- Publisher
- Install Path
- Installed by
- Removed Applications
- Uninstall Date
- Uninstalled Version
- Publisher
- Uninstalled by
- Windows Logs
- Application
- Security
- Setup
- System
- Forwarded Events
- Application and Service Logs
- Hardware Events
- Key Management Service
- Microsoft
- Microsoft Office Alerts
- Windows PowerShell
- Pending Reboot
- System Uptime
- Bitlocker Enabled?
- Bluetooth enabled
- Bluetooth connected
- Authenticated Users
- Registered Domain
- Windows Defender
- Windows Firewall
- Services
- Startup Processes
- Running Processes
- Consumed Memory
- Consumed Processor
- Consumed Disk
- Consumed Network
- Geographic location
- Group Policies applied
- Local Policies applied
- Device Drivers in use
- Device Driver versions
- Firmware version
- Intune Policy applied
- Configuration Manager Policy
- Power Options
- User Accounts
Why should you choose cloud-based RMM Software?
When it comes to comparing a cloud-based RMM to a legacy on-prem solution, it's easy to see that cloud-based checks all the boxes.
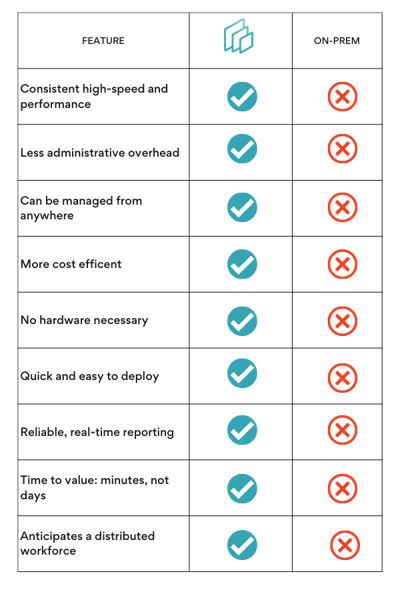
Your users aren't all on prem...why is your monitoring solution?
RMM stands for Remote Monitoring and Management. We think it should also stand for Risk Mitigation and Management - that is what we are all working to solve.
Effective RMM software is designed to help IT teams remotely and proactively manage, secure, and provision company resources.
Those resources can be end-user computers, mobile devices, and even remote networks. Gone are the days of needing to send a SysAdmin halfway across the country to configure a vpn.
For a product to be considered an RMM, it product needs to meet the following criteria.
- Ability to discover and track IT-related issues.
- Monitor IT assets such as applications, computers, and endpoints, servers, and devices.
- Provide access to remote administrators to access, assess, alert, automate, secure, and fix endpoints.
- Increase and monitor network performance, availability, and security.
- Learn over time, add value as the system learns.
- Work with technology standards and investments the organization has already made
500,000,000 people wanted to work remotely - and then they got their wish. We don't think they are coming back anytime soon.
Our teams need unified systems to stich together the data and metrics we need.
There are lots of advantages for companies or Managed Service Providers (MSPs) using RMMs, including:
- Increased visibility into security posture
- Ability to maintain a healthy network
- Remote access management for IT troubleshooting
- Automating repeatable tasks
- IT management in a single control panel
- Trending, Alerting, Planning, Configuration Drift
Our users, networks, and resources are now distributed to the four corners of the planet.
Our solutions need to take this as a given.
Traditional RMM platforms only monitor standard metrics like CPU, memory, disk, and network performance. Very few take into account the new reality of massively distributed teams.
In addition to these standard metrics, Remotely also monitors and reports on network configuration and environmental details, NIST CVE Alerts, storage encryption, and more. See the full list of metrics we measure.
Here are the three core jobs that RMM solutions are used for:
Behind-the-scenes remote maintenance & remediation.
RMM software supports technicians in managing updates, running scripts, and deploying software while providing remote connections for machines to allow for troubleshooting without end-user interruption.
IT Management Automation.
RMM software solutions crack open access to streamline workflows and automate countless IT tasks, whether that’s running scripts, responding to tickets, or installing patches, all of it can be done through RMM.
Remote Monitoring & Alerts.
With RMM solutions, companies can enjoy 24/7 monitoring for the health and performance of individual systems and entire networks. IT professionals can enjoy ongoing monitoring of disruptive issues, have automated workflows that help address alerts, and have reports generated that offer clear visibility into every aspect of your network. Additionally, RMMs are used to deploy and actively manage endpoint security for third parties and security products.
The needs and priorities of your company determine whether or not RMM software is right for you, and right for you at this time. However, here are 5 things to keep in mind when researching or vetting a RMM software:
- Reliability
- Security
- Ease-of-use
- Integration with current tools
- Real-time data
- Remote - First / Distributed Architecture
Some — but not all — RMM software monitors and reports on performance and security metrics in real-time. At Remotely, we believe you can't make informed decisions with old data, so as much as possible of our reporting is done in real-time.
Sometimes historical, trending, or pattern data streams can be used together with real-time information.
.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)