The Remote Endpoint Risk Paradox
by Tyler Rohrer on December 5, 2022
Distinguished Google engineer Jeff Dean once said that the job of those of us engaged in computer science is "to create reliable computer systems, out of intrinsically unreliable parts". Let's face it - we are typically charged with designing, testing, and deploying technology with a acceptable levels of uncertainty, which gets factored into our stacks. It is this gap bad actors seek to exploit. It is this gap we endeavor to solve
Many among us would also agree that often times - remote end users are the most unreliable parts in our stack. Human error - often unintentional or unaware of consequences is so variable we face a true paradox. The real problem exists between chair and keyboard ;) End users, human error, sentient disobedience and bad networks at Starbucks are all headwinds we must contend with in our missions.
We want to create "reliable" aka "productive" systems for .png?width=318&height=318&name=you%20cant%20patch%20stupid%20(1).png) end users so they can consume and create the content we ask them to as a function of their jobs. We want resources to be available when, how, and where our users now prefer to use them to delivery productive results. We know that any interruption to their digital day based on the lack of a resource, setting, document, or security disruption, is no longer theoretical.
end users so they can consume and create the content we ask them to as a function of their jobs. We want resources to be available when, how, and where our users now prefer to use them to delivery productive results. We know that any interruption to their digital day based on the lack of a resource, setting, document, or security disruption, is no longer theoretical.
Bad actors, regulatory compliance, and cyber risk insurance are no longer buzz words but rather appear in our companies financial statements as line items that must now be managed. This is the new normal.
Naturally such an observation leads us to then ask - how do we add reliability? How do we gain/validate/grant "trust" ? How do I contend with the decisions of the past few years to allow major portions of my user base to use net new devices, with local administrator rights and privileges, and lax rules?
Adding policies, processes, or constraints on our end users will be met with near revolt - and certainly complaints of lost productivity. The more control we seek to exert on those systems to mitigate risk, the more we threaten productivity. The will of our end users is often as important as the device they sit at. Therein lies the paradox. We can lock systems down to near crippling levels, create read only volumes, ephemeral runtimes, non-persistence and data encryption. This overhead clearly hinders end user experience aka productivity.
 We know we cannot leave the systems wide open, allowing every toolbar, reddit suggested app, or searched shortcut hack to find their way onto machines, and potentially onto our networks through vpn's at the speed of light.
We know we cannot leave the systems wide open, allowing every toolbar, reddit suggested app, or searched shortcut hack to find their way onto machines, and potentially onto our networks through vpn's at the speed of light.
We can do two things however. Both are getting easier.
We can look and see where the actual risk is on and across our end users and endpoints. Then we can write software that reacts when either of those change. Simply stated we proceed with zero trust, but go one step deeper looking for what we should not trust. We then isolate, address/remediate, and continue to watch and validate risk elements are removed. It is now an ongoing process, not a static exercise.
We built RemotelyRMM to help turn on the lights in the dark room of remote work and surface exactly this kind of information. We have written on the technical elements of our solution here, and believe any Risk Management Framework discussion must be evidence based. And not point in time evidence, but living data streams that capture the real world production environment you must contend with, secure, support.
Decision support using live data is the new gold/oil as we can now either manually or systemically write processes that react to changes, drift, or, new RISK. We should all aspire to automate the mundane, and often time system settings, policies, or routines at scale can not only save us massive time and budget, but allow us to finally get back to higher priority missions within your organization. An enterprise IF/THEN/THEN engine would be very helpful and deliver adaptive policy management options back to us.
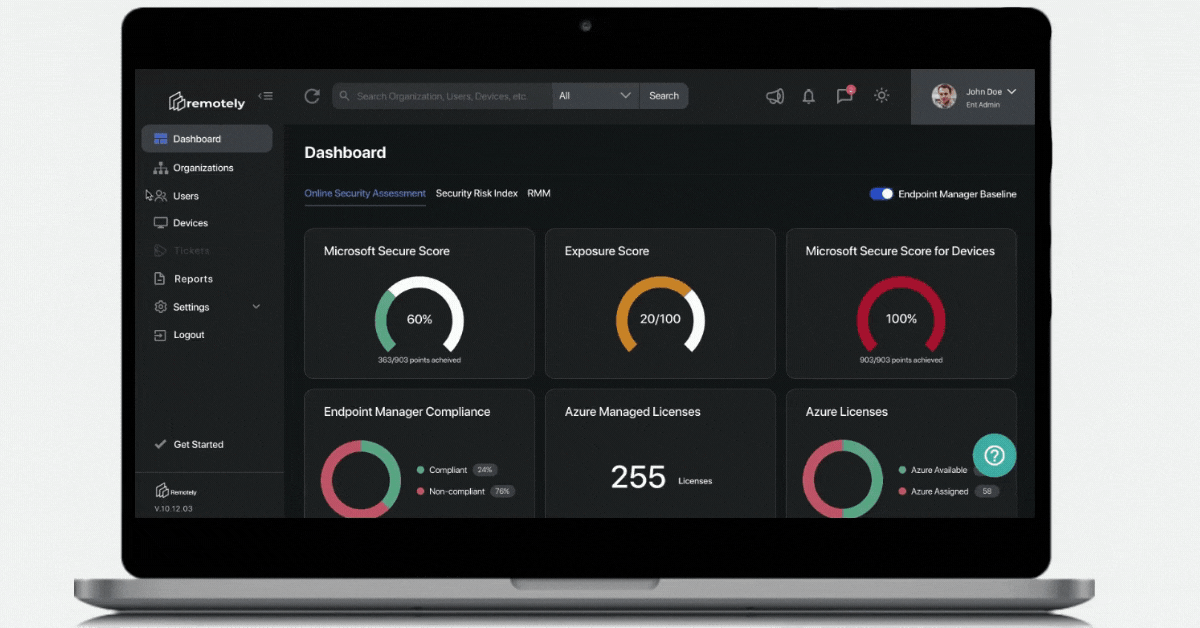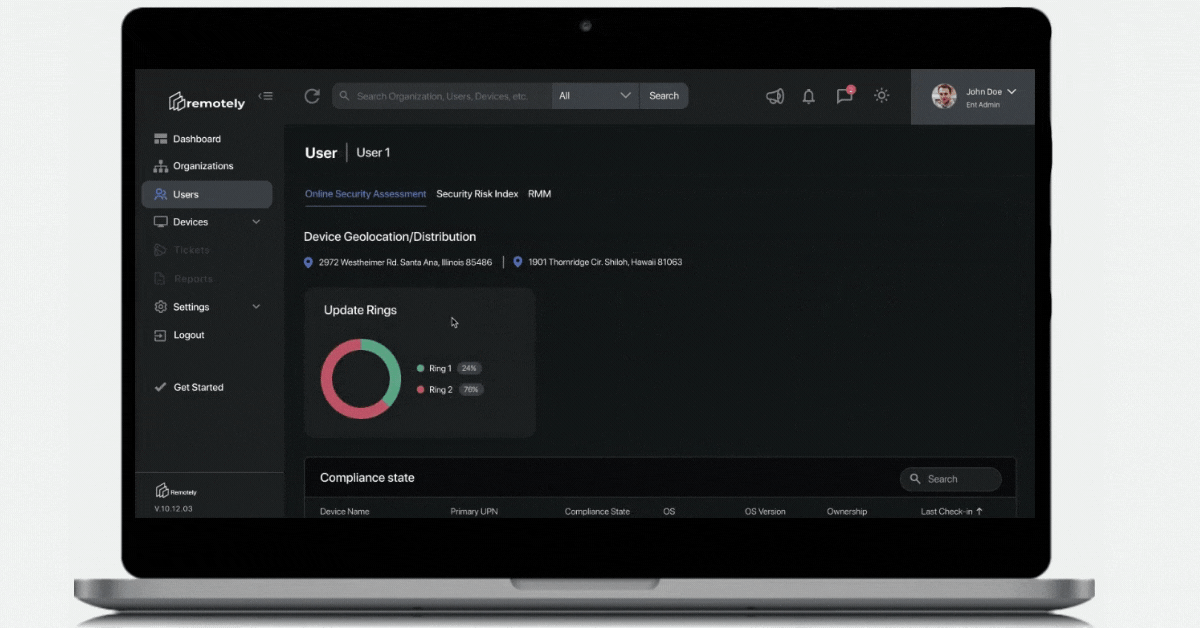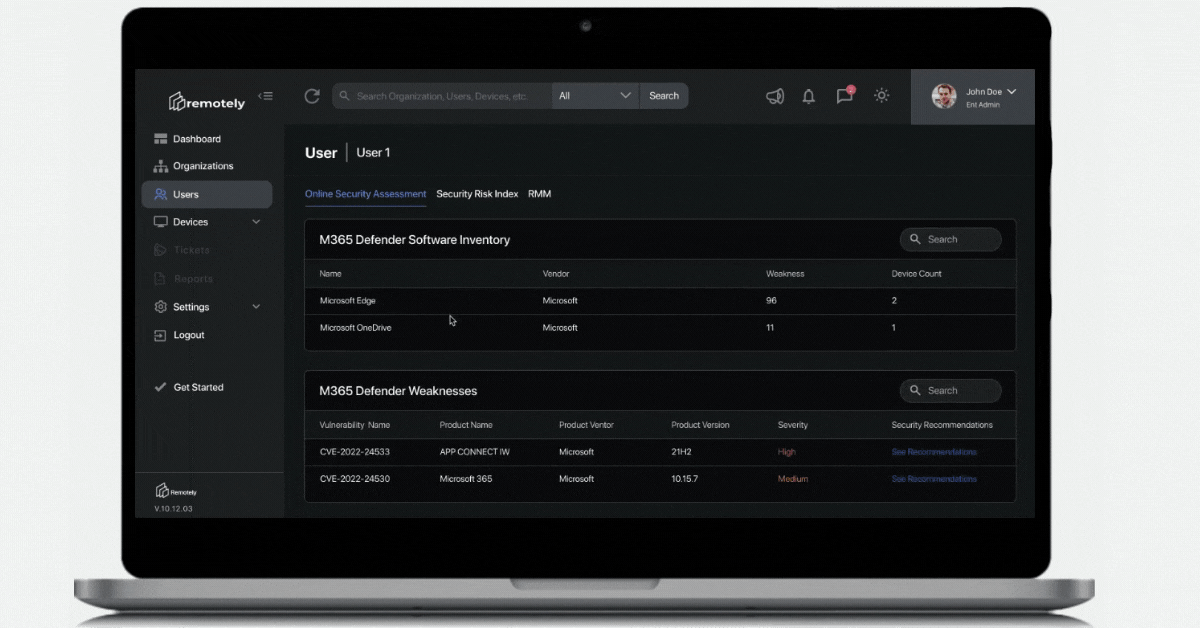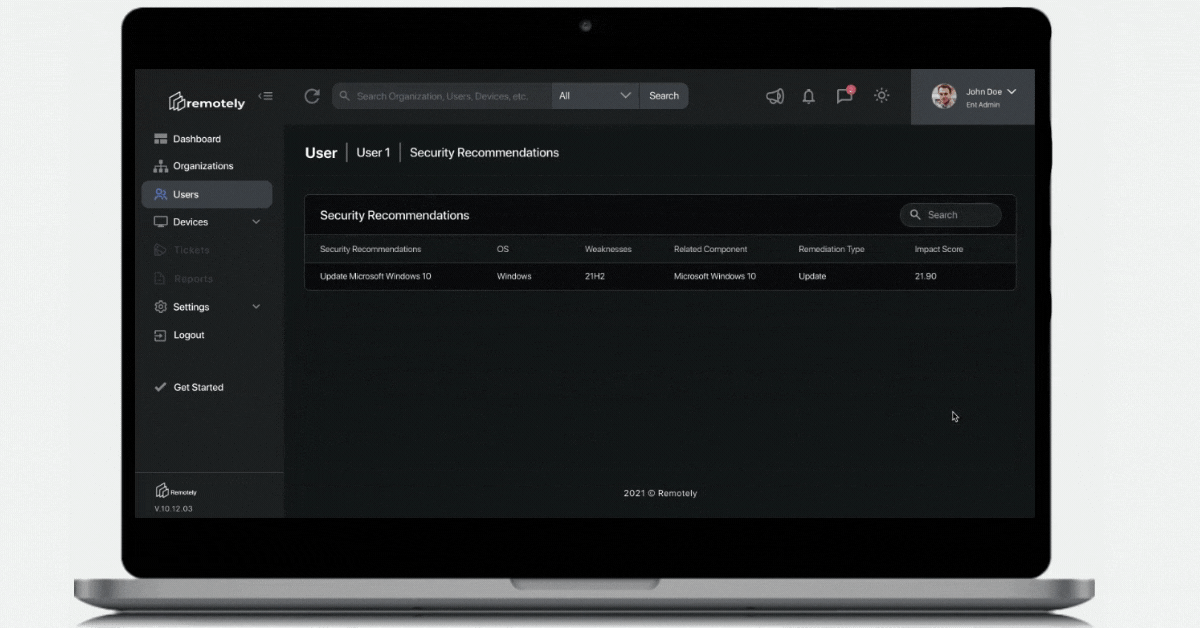
The system administrator and security professionals remote user paradox is solved not by one magic product, or vendor, nor can it be - they don't know your business like you do. The paradox is solved with a methodology. Assessing, addressing, and then validating each solution is making progress in your key metrics is important as often technology enchantment can cause lost cycles.
We see more and more cloud consumption of specifically Microsoft Azure services ranging from Active Directory, to Teams, Office 365, Microsoft Security Solutions like Defender, Advanced Threat Protection, Sentinel, Intune, Endpoint Manager, among others. These services provide massive opportunity to begin to "turn knobs" at scale - and begin to set up "reactive" versus static policies. We will be diving into this notion of adaptive policy management as a core component of any enterprise endpoint risk management framework.
We at Remotely Inc. are sharing a Risk Management Framework For Enterprise End Users and Endpoints - however - every one of us is now writing the book on how to best solve this paradox. Understanding as much as we can - by measuring and monitoring BOTH the edge, and the cloud side of our users digital day.
We welcome your feedback not only in our thoughts on RMF methodology, but also with our roadmap. While we are each writing the pages of the future of remote work - everyone can join in the chorus!
Thanks - be safe out there / shields up.
T.Rex
Add some fun, compelling content here
- Cyber Security (16)
- Security (15)
- Azure (10)
- Cyberattack (10)
- IT Operations Management (10)
- Remote Monitoring and Management (10)
- AIP (9)
- IT Strategy (9)
- Remote Work (9)
- Asset Management (7)
- IT Operations (6)
- Asset Inventory (5)
- Reliability (5)
- Remotely Interesting (5)
- Risk Management Framework (5)
- Azure Migration (4)
- Microsoft Secure Score (4)
- Office 365 (4)
- Security Risk Index (4)
- Customer Success (3)
- GRC (3)
- Risk Dashboard (3)
- Support (3)
- Powershell (2)
- First Steps (1)
- Migrate (1)
- System Requirements (1)
- Virtual Machine (1)
- Zero Trust (1)
- August 1, 2023 (1)
- July 1, 2023 (2)
- May 1, 2023 (1)
- March 1, 2023 (2)
- February 1, 2023 (1)
- January 1, 2023 (1)
- December 1, 2022 (2)
- November 1, 2022 (2)
- October 1, 2022 (1)
- September 1, 2022 (2)
- August 1, 2022 (1)
- July 1, 2022 (1)
- June 1, 2022 (2)
- May 1, 2022 (4)
- April 1, 2022 (3)
- March 1, 2022 (2)
- February 1, 2022 (2)
- January 1, 2022 (1)
- December 1, 2021 (4)
- November 1, 2021 (1)
- October 1, 2021 (1)
.png?width=50&height=50&name=Untitled%20(50%20%C3%97%2050%20px).png)


No Comments Yet
Let us know what you think